Search N5 Net Software Repository:
Search Files
Sponsor:
Browse:
- Audio & Multimedia (1565)
- Business (1732)
- Communications (466)
- Desktop (182)
- Development (569)
- Education (166)
- Games & Entertainment (707)
- Graphic Apps (683)
- Home & Hobby (105)
- Network & Internet (543)
- Security & Privacy (500)
- Servers (65)
- System Utilities (9315)
- Web Development (281)
Areas Of Interest
Authors Area
Are you a software author? Take a look at our Author Resource Center where you will find marketing tools, software specifically created for promoting your software and a ton of other helpful resources.
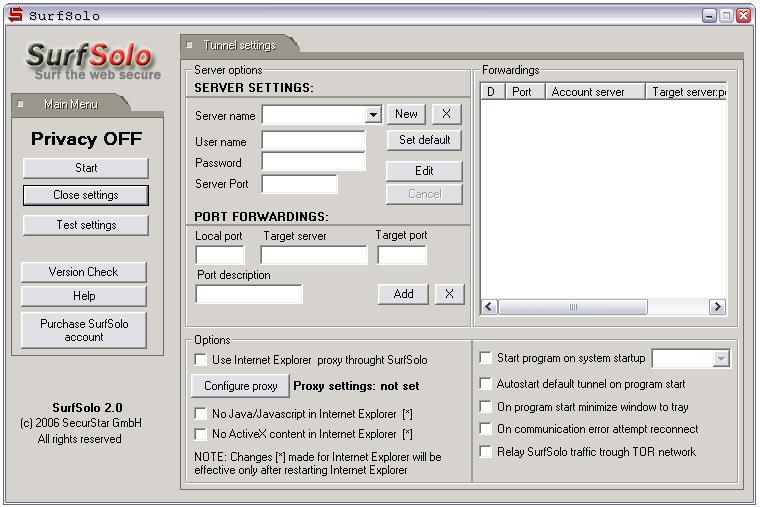
SurfSolo 2.0
No one knows more about ?surfing? and downloading habits than your ISP (Internet Service Provider). The ISP is able to know who you are, every site you visit, every page you view, and every file you download. How this happens? Every time you are connected on the Internet your ISP gives you an IP number that is a unique address which identifies you from the other computers on the network living you vunerable to any attacks from hackers or eavesdroppers. SurfSolo was created to protect you from those problems. Powerful software that allows the user to get totally anonymous and at the same time protects the data exchange on the Internet.The software provides a direct encrypted link(by using SSH Protocol) with one of the world wide SecurStar high bandwidth security proxy servers. ?SSH protocol (Secure Shell protocol)? which makes the connection encrypted from your personal computer to any website. A protocol says which format the data is going to be sent and which rules will be applied. The SSH protocol creates a ?virtual tunnel?, in such a way you are totally invisible from any kind of monitoring. If someone tries to track your IP number, it will recognize only our SecurStar server's IP, so it would be impossible to track your personal IP number. The SurfSolo also provides free e-mail account (no mailbox size limit). Sending emails from it will not reveal your personal IP number. At the moment SecurStar has 5 proxy servers available around the world (Malaysia, Hong Kong, Germany, Holland and Czech Republic).When the customer purchases the software he can choose one of the Proxy servers available.
Specifications:
Version: 2.0 |
Download
|
Similar Products:
Security & Privacy :: Other
 Privacy Eraser is an all-in-one privacy suite, PC optimization and cleaning tool. It cleans all of your internet history traces and past activities with one click, recovers hard drive space by deleting unnecessary and redundant files, speeds up internet surfing and browsing, boosts your PC's performance and stability making it faster, secure and more efficient.
Privacy Eraser is an all-in-one privacy suite, PC optimization and cleaning tool. It cleans all of your internet history traces and past activities with one click, recovers hard drive space by deleting unnecessary and redundant files, speeds up internet surfing and browsing, boosts your PC's performance and stability making it faster, secure and more efficient.
Windows | Freeware
Read More
Security & Privacy :: Other
 Privacy Eraser is an all-in-one privacy suite, PC optimization and cleaning tool. It cleans all of your internet history traces and past activities with one click, recovers hard drive space by deleting unnecessary and redundant files, speeds up internet surfing and browsing, boosts your PC's performance and stability making it faster, secure and more efficient.
Privacy Eraser is an all-in-one privacy suite, PC optimization and cleaning tool. It cleans all of your internet history traces and past activities with one click, recovers hard drive space by deleting unnecessary and redundant files, speeds up internet surfing and browsing, boosts your PC's performance and stability making it faster, secure and more efficient.
Windows | Freeware
Read More
PASSWORD SECURITY SCANNER 1.65
Security & Privacy :: Other
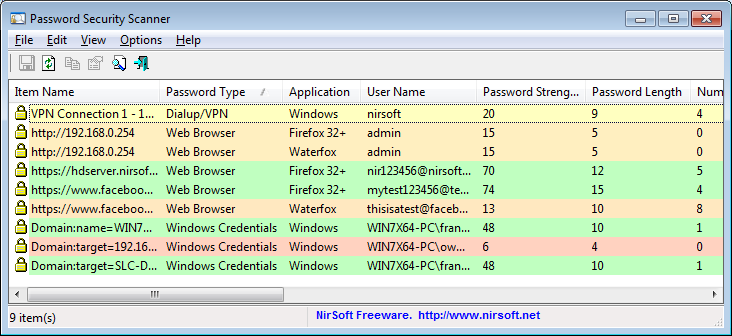 This utility scans the passwords stored by popular Windows applications (Microsoft Outlook, Internet Explorer, Mozilla Firefox, and more...) and displays security information about all these passwords. The security information of every stored password includes the total number of characters, number of numeric characters, number of lowercase/uppercase characters, number of repeating characters, and password strength.
This utility scans the passwords stored by popular Windows applications (Microsoft Outlook, Internet Explorer, Mozilla Firefox, and more...) and displays security information about all these passwords. The security information of every stored password includes the total number of characters, number of numeric characters, number of lowercase/uppercase characters, number of repeating characters, and password strength.
Windows | Freeware
Read More
Security & Privacy :: Other
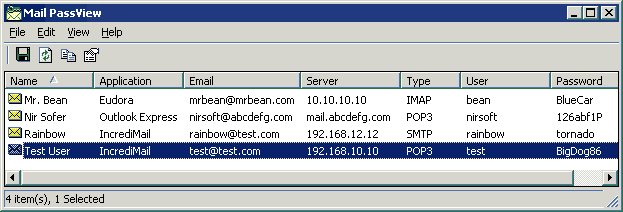 Mail PassView is a small password-recovery tool that reveals the passwords and other account details for the following email clients:
Outlook Express
Microsoft Outlook 2000 (POP3 and SMTP Accounts only)
Microsoft Outlook 2002/2003 (POP3, IMAP, HTTP and SMTP Accounts)
IncrediMail
Eudora
Netscape 6.x/7.x
Mozilla Thunderbird
Group Mail Free
Web-based email clients
Mail PassView is a small password-recovery tool that reveals the passwords and other account details for the following email clients:
Outlook Express
Microsoft Outlook 2000 (POP3 and SMTP Accounts only)
Microsoft Outlook 2002/2003 (POP3, IMAP, HTTP and SMTP Accounts)
IncrediMail
Eudora
Netscape 6.x/7.x
Mozilla Thunderbird
Group Mail Free
Web-based email clients
Windows | Freeware
Read More