Search N5 Net Software Repository:
Search Files
Sponsor:
Browse:
- Audio & Multimedia (1596)
- Business (4238)
- Communications (1258)
- Desktop (183)
- Development (602)
- Education (171)
- Games & Entertainment (702)
- Graphic Apps (686)
- Home & Hobby (107)
- Network & Internet (571)
- Security & Privacy (532)
- Servers (65)
- System Utilities (11196)
- Web Development (284)
Areas Of Interest
Authors Area
Are you a software author? Take a look at our Author Resource Center where you will find marketing tools, software specifically created for promoting your software and a ton of other helpful resources.
Data Destroyer 17.07
When Windows 'deletes' a file it does not actually destroy the contents of the file but rather simply unlinks the file from the file directory system, leaving the contents of the file in the disk sectors. This data will remain there until the operating system uses those sectors when writing new data. Until the old data is overwritten (which take months or longer) it can be recovered by programs that read disk sectors directly, such as forensic software (so called because it is used to obtain evidence in criminal investigations and also in legal discovery). In order to be sure that a deleted file really is deleted, gone for good, its contents never to be seen again, it is necessary to overwrite the data sectors of that file. Data Destroyer purges data in files, where 'purge' means to destroy, to eliminate completely by overwriting, so that the data cannot be recovered by any means. Data Destroyer allows you to destroy the contents of a file by overwriting it several times (or many times) with random bytes, and with bytes with alternating bit patterns, before the file is deleted. Data Destroyer can purge: a single file, all files in a folder, all files in a folder and all files in its subfolders, a specified subset of files in a folder and (optionally) in its subfolders, all files whose file dates are before a specified date, all files in selected subfolders (or in selected subfolders of a folder). It can also purge files in the Windows 7 and 8 Recycle Bin. This software checks for possible errors in user input, and is designed to minimize the chance of accidentally purging a file that you wish to keep. Another feature of Data Destroyer is that you can get an estimate of the time required to perform a purge operation.
Specifications:
Version: 17.07 |
Download
|
Similar Products:
Security & Privacy :: Other
 Privacy Eraser is an all-in-one privacy suite, PC optimization and cleaning tool. It cleans all of your internet history traces and past activities with one click, recovers hard drive space by deleting unnecessary and redundant files, speeds up internet surfing and browsing, boosts your PC's performance and stability making it faster, secure and more efficient.
Privacy Eraser is an all-in-one privacy suite, PC optimization and cleaning tool. It cleans all of your internet history traces and past activities with one click, recovers hard drive space by deleting unnecessary and redundant files, speeds up internet surfing and browsing, boosts your PC's performance and stability making it faster, secure and more efficient.
Windows | Freeware
Read More
Security & Privacy :: Other
 Privacy Eraser is an all-in-one privacy suite, PC optimization and cleaning tool. It cleans all of your internet history traces and past activities with one click, recovers hard drive space by deleting unnecessary and redundant files, speeds up internet surfing and browsing, boosts your PC's performance and stability making it faster, secure and more efficient.
Privacy Eraser is an all-in-one privacy suite, PC optimization and cleaning tool. It cleans all of your internet history traces and past activities with one click, recovers hard drive space by deleting unnecessary and redundant files, speeds up internet surfing and browsing, boosts your PC's performance and stability making it faster, secure and more efficient.
Windows | Freeware
Read More
PASSWORD SECURITY SCANNER 1.65
Security & Privacy :: Other
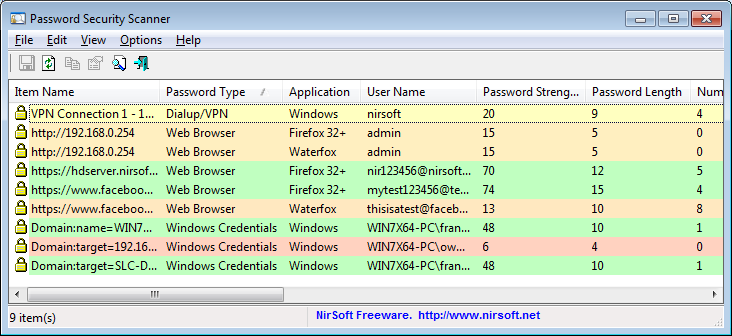 This utility scans the passwords stored by popular Windows applications (Microsoft Outlook, Internet Explorer, Mozilla Firefox, and more...) and displays security information about all these passwords. The security information of every stored password includes the total number of characters, number of numeric characters, number of lowercase/uppercase characters, number of repeating characters, and password strength.
This utility scans the passwords stored by popular Windows applications (Microsoft Outlook, Internet Explorer, Mozilla Firefox, and more...) and displays security information about all these passwords. The security information of every stored password includes the total number of characters, number of numeric characters, number of lowercase/uppercase characters, number of repeating characters, and password strength.
Windows | Freeware
Read More
Security & Privacy :: Other
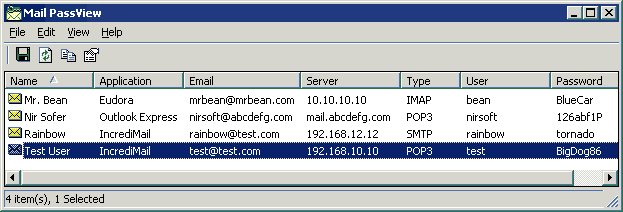 Mail PassView is a small password-recovery tool that reveals the passwords and other account details for the following email clients:
Outlook Express
Microsoft Outlook 2000 (POP3 and SMTP Accounts only)
Microsoft Outlook 2002/2003 (POP3, IMAP, HTTP and SMTP Accounts)
IncrediMail
Eudora
Netscape 6.x/7.x
Mozilla Thunderbird
Group Mail Free
Web-based email clients
Mail PassView is a small password-recovery tool that reveals the passwords and other account details for the following email clients:
Outlook Express
Microsoft Outlook 2000 (POP3 and SMTP Accounts only)
Microsoft Outlook 2002/2003 (POP3, IMAP, HTTP and SMTP Accounts)
IncrediMail
Eudora
Netscape 6.x/7.x
Mozilla Thunderbird
Group Mail Free
Web-based email clients
Windows | Freeware
Read More




