Search N5 Net Software Repository:
Search Files
Sponsor:
Browse:
- Audio & Multimedia (1565)
- Business (1732)
- Communications (466)
- Desktop (182)
- Development (569)
- Education (166)
- Games & Entertainment (707)
- Graphic Apps (683)
- Home & Hobby (105)
- Network & Internet (543)
- Security & Privacy (500)
- Servers (65)
- System Utilities (9315)
- Web Development (281)
Areas Of Interest
Authors Area
Are you a software author? Take a look at our Author Resource Center where you will find marketing tools, software specifically created for promoting your software and a ton of other helpful resources.
XorIt 1.9
Security & Privacy :: Encryption Tools
Most file encryptors use methods that rely on the theory of computational security, that is difficulty of key factorisation prevents decryption of the file. But this method may not work forever. It used to be considered that a 56 bit key was unbreakable to brute force attacks, but the government of the USA now requires all Top Secret data to use keys of at least 192 bits. This bar will keep raising as computing power increases. (It is argued by some though that this will never happen due to the laws of physics!) XorIt is designed to use conventional XOR encryption on keys that are the same size as the file to be encrypted. Furthermore, if you use an unpredictable file that is the same size (or larger) than the original file and you use this file only once, this is known as a "one-time pad" and it is completely unbreakable, even to computers 1000 years from now. This is because there is no algorithm at all, just a big key, and thus there is no pattern to follow once you have decrypted any part of the file. Thus attempts to decrypt it could result in any file, and there would be no way to verify that it has decrypted correctly. XorIt is written in Assembly Language for maximum efficiency. XorIt is a simplified version of our program CryptIt.
Specifications:
Version: 1.9 |
Download
|
Similar Products:
ARMORTOOLS PROFESSIONAL 26.2.1
Security & Privacy :: Encryption Tools
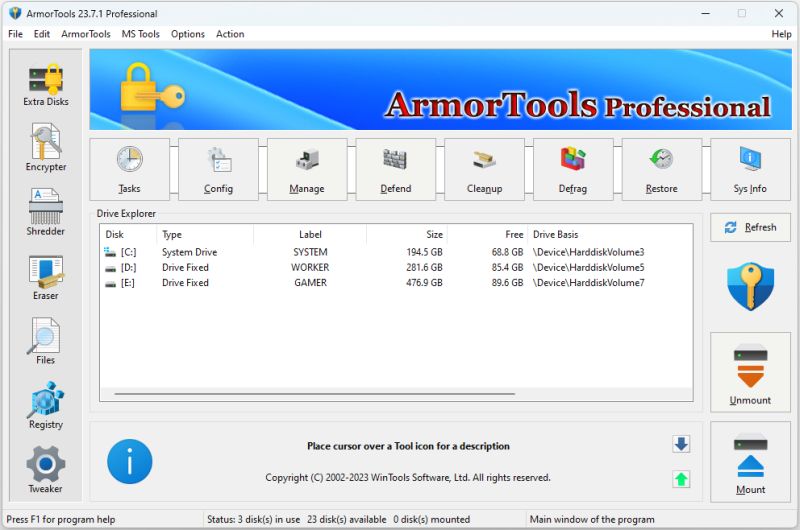 ArmorTools Professional is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
ArmorTools Professional is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
Windows | Shareware
Read More
System Utilities :: Text/Document Editors
Windows | Shareware
Read More
System Utilities :: File & Disk Management
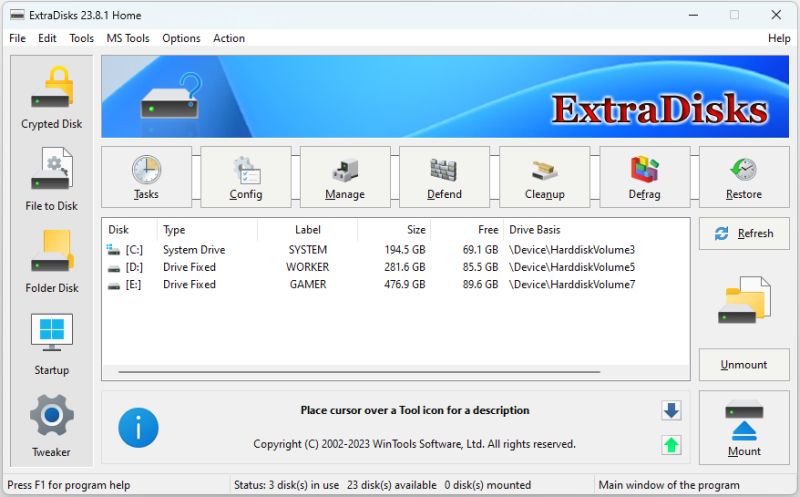 ExtraDisks is a suite of tools for creating Virtual disks on your computer - physical drives remain unchanged and are not divided into additional partitions. The program contains tools for creating Encrypted disks, Virtual disks based on files and Virtual disks based on folders. The current version consists of the following tools: Encrypted Disks, Virtual Disks, Folder Disks, Startup Manager, System Tweaker.
ExtraDisks is a suite of tools for creating Virtual disks on your computer - physical drives remain unchanged and are not divided into additional partitions. The program contains tools for creating Encrypted disks, Virtual disks based on files and Virtual disks based on folders. The current version consists of the following tools: Encrypted Disks, Virtual Disks, Folder Disks, Startup Manager, System Tweaker.
Windows | Shareware
Read More
Security & Privacy :: Encryption Tools
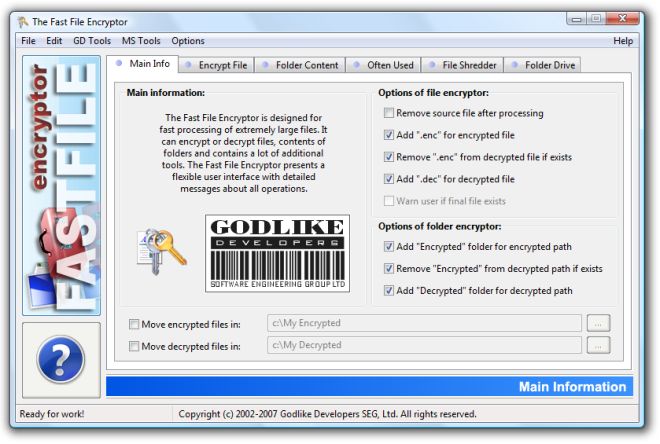 Fast File Encryptor is MS Windows compatible software designed for fast processing of extremely large files. It can encrypt and decrypt files, contents of folders using any file as a password. Fast File Encryptor contains a lot of additional tools and presents a flexible user interface with detailed messages about all operations. Fast File Encryptor compatible with ArmorTools software.
Fast File Encryptor is MS Windows compatible software designed for fast processing of extremely large files. It can encrypt and decrypt files, contents of folders using any file as a password. Fast File Encryptor contains a lot of additional tools and presents a flexible user interface with detailed messages about all operations. Fast File Encryptor compatible with ArmorTools software.
Windows | Shareware
Read More




