Search N5 Net Software Repository:
Search Files
Sponsor:
Browse:
- Audio & Multimedia (1565)
- Business (1732)
- Communications (466)
- Desktop (182)
- Development (569)
- Education (166)
- Games & Entertainment (707)
- Graphic Apps (683)
- Home & Hobby (105)
- Network & Internet (543)
- Security & Privacy (500)
- Servers (65)
- System Utilities (9315)
- Web Development (281)
Areas Of Interest
Authors Area
Are you a software author? Take a look at our Author Resource Center where you will find marketing tools, software specifically created for promoting your software and a ton of other helpful resources.
Downloading RemoteDirDetector 2.0
Your download will begin in a few seconds. If it does not start you can download directly through one of the mirror sites below.
- Mirror Site 1: http://securityxploded.com/getfile.php?id=7651
Get Details for RemoteDirDetector 2.0
Similar Products:
Security & Privacy :: Other
 Privacy Eraser is an all-in-one privacy suite, PC optimization and cleaning tool. It cleans all of your internet history traces and past activities with one click, recovers hard drive space by deleting unnecessary and redundant files, speeds up internet surfing and browsing, boosts your PC's performance and stability making it faster, secure and more efficient.
Privacy Eraser is an all-in-one privacy suite, PC optimization and cleaning tool. It cleans all of your internet history traces and past activities with one click, recovers hard drive space by deleting unnecessary and redundant files, speeds up internet surfing and browsing, boosts your PC's performance and stability making it faster, secure and more efficient.
Windows | Freeware
Read More
Security & Privacy :: Other
 Privacy Eraser is an all-in-one privacy suite, PC optimization and cleaning tool. It cleans all of your internet history traces and past activities with one click, recovers hard drive space by deleting unnecessary and redundant files, speeds up internet surfing and browsing, boosts your PC's performance and stability making it faster, secure and more efficient.
Privacy Eraser is an all-in-one privacy suite, PC optimization and cleaning tool. It cleans all of your internet history traces and past activities with one click, recovers hard drive space by deleting unnecessary and redundant files, speeds up internet surfing and browsing, boosts your PC's performance and stability making it faster, secure and more efficient.
Windows | Freeware
Read More
PASSWORD SECURITY SCANNER 1.65
Security & Privacy :: Other
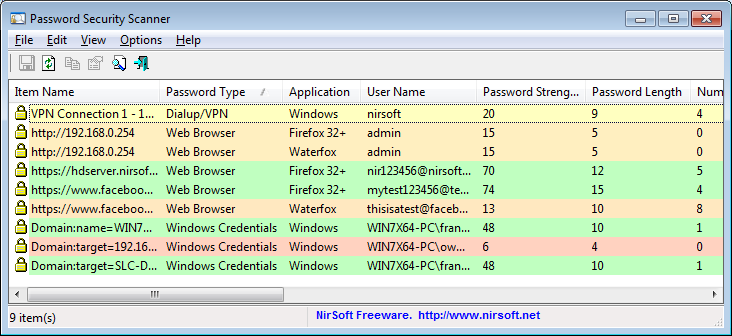 This utility scans the passwords stored by popular Windows applications (Microsoft Outlook, Internet Explorer, Mozilla Firefox, and more...) and displays security information about all these passwords. The security information of every stored password includes the total number of characters, number of numeric characters, number of lowercase/uppercase characters, number of repeating characters, and password strength.
This utility scans the passwords stored by popular Windows applications (Microsoft Outlook, Internet Explorer, Mozilla Firefox, and more...) and displays security information about all these passwords. The security information of every stored password includes the total number of characters, number of numeric characters, number of lowercase/uppercase characters, number of repeating characters, and password strength.
Windows | Freeware
Read More
Security & Privacy :: Other
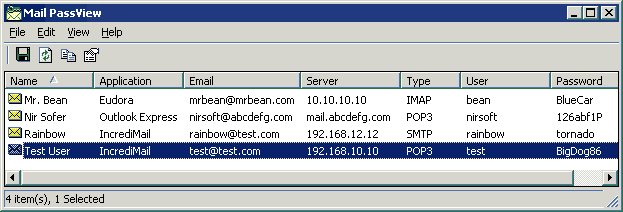 Mail PassView is a small password-recovery tool that reveals the passwords and other account details for the following email clients:
Outlook Express
Microsoft Outlook 2000 (POP3 and SMTP Accounts only)
Microsoft Outlook 2002/2003 (POP3, IMAP, HTTP and SMTP Accounts)
IncrediMail
Eudora
Netscape 6.x/7.x
Mozilla Thunderbird
Group Mail Free
Web-based email clients
Mail PassView is a small password-recovery tool that reveals the passwords and other account details for the following email clients:
Outlook Express
Microsoft Outlook 2000 (POP3 and SMTP Accounts only)
Microsoft Outlook 2002/2003 (POP3, IMAP, HTTP and SMTP Accounts)
IncrediMail
Eudora
Netscape 6.x/7.x
Mozilla Thunderbird
Group Mail Free
Web-based email clients
Windows | Freeware
Read More
Security & Privacy :: Other
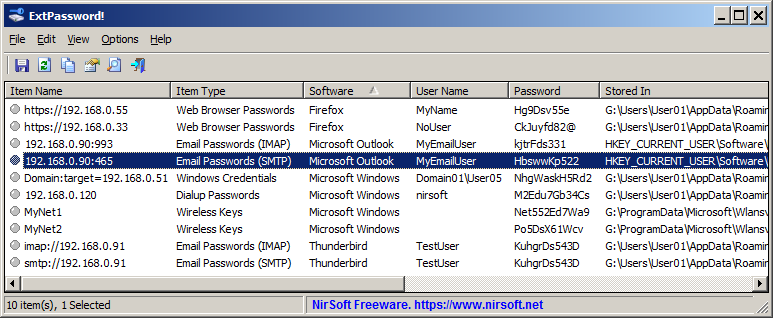 ExtPassword! is tool for Windows that allows you to recover passwords stored on external drive plugged to your computer.
ExtPassword! can decrypt and extract multiple types of passwords and essential information, including passwords of common Web browsers, passwords of common email software, dialup/VPN passwords, wireless network keys, Windows network credentials, Windows product key, Windows security questions.
ExtPassword! is tool for Windows that allows you to recover passwords stored on external drive plugged to your computer.
ExtPassword! can decrypt and extract multiple types of passwords and essential information, including passwords of common Web browsers, passwords of common email software, dialup/VPN passwords, wireless network keys, Windows network credentials, Windows product key, Windows security questions.
Windows | Freeware
Read More
Security & Privacy :: Other
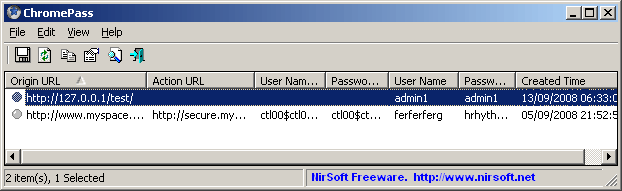 ChromePass is a small password recovery tool that allows you to view the user names and passwords stored by Google Chrome Web browser. For each password entry, the following information is displayed: Origin URL, Action URL, User Name Field, Password Field, User Name, Password, and Created Time.
You can select one or more items and then save them into text/html/xml file or copy them to the clipboard.
ChromePass is a small password recovery tool that allows you to view the user names and passwords stored by Google Chrome Web browser. For each password entry, the following information is displayed: Origin URL, Action URL, User Name Field, Password Field, User Name, Password, and Created Time.
You can select one or more items and then save them into text/html/xml file or copy them to the clipboard.
Windows | Freeware
Read More
Security & Privacy :: Other
 Permanent Delete is a free utility that can be used to delete files/folders permanently so that no software can recover these files. You can choose from 3 deletion methods from fast and secure enough to slow and extremely secure.
Permanent Delete is a free utility that can be used to delete files/folders permanently so that no software can recover these files. You can choose from 3 deletion methods from fast and secure enough to slow and extremely secure.
Windows | Freeware
Read More
Security & Privacy :: Other
 File Monster completely erases files from your system -- actually overwriting the information in the file so it can not be recovered. The reason information is still available when you delete files with normal deletion methods is because normal deletion methods only tell the operating system to not recognize the file as being present anymore, yet the information hasn't really been erased.
File Monster completely erases files from your system -- actually overwriting the information in the file so it can not be recovered. The reason information is still available when you delete files with normal deletion methods is because normal deletion methods only tell the operating system to not recognize the file as being present anymore, yet the information hasn't really been erased.
Windows | Shareware
Read More
Security & Privacy :: Other
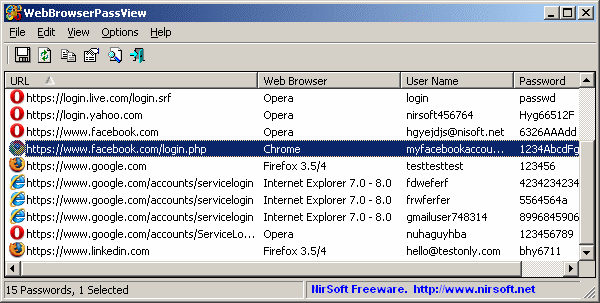 WebBrowserPassView is a password recovery tool that reveals the passwords stored by the following Web browsers: Internet Explorer (Version 4.0 - 8.0), Mozilla Firefox (All Versions), Google Chrome, and Opera. This tool can be used to recover your lost/forgotten password of any Website, including popular Web sites, like Facebook, Yahoo, Google, and GMail, as long as the password is stored by your Web Browser.
WebBrowserPassView is a password recovery tool that reveals the passwords stored by the following Web browsers: Internet Explorer (Version 4.0 - 8.0), Mozilla Firefox (All Versions), Google Chrome, and Opera. This tool can be used to recover your lost/forgotten password of any Website, including popular Web sites, like Facebook, Yahoo, Google, and GMail, as long as the password is stored by your Web Browser.
Windows | Freeware
Read More


