Search N5 Net Software Repository:
Search Files
Sponsor:
Browse:
- Audio & Multimedia (1570)
- Business (4232)
- Communications (1254)
- Desktop (183)
- Development (597)
- Education (166)
- Games & Entertainment (706)
- Graphic Apps (681)
- Home & Hobby (106)
- Network & Internet (571)
- Security & Privacy (526)
- Servers (65)
- System Utilities (11354)
- Web Development (285)
Areas Of Interest
Authors Area
Are you a software author? Take a look at our Author Resource Center where you will find marketing tools, software specifically created for promoting your software and a ton of other helpful resources.
Downloading File Encryptor 26.0.1
Your download will begin in a few seconds. If it does not start you can download directly through one of the mirror sites below.
- Mirror Site 1: http://www.fastencryptor.com/setup_fileencryptor.exe
Get Details for File Encryptor 26.0.1
Similar Products:
System Utilities :: File & Disk Management
 ExtraDisks is a suite of tools for creating Virtual disks on your computer - physical drives remain unchanged and are not divided into additional partitions. The program contains tools for creating Encrypted disks, Virtual disks based on files and Virtual disks based on folders. The current version consists of the following tools: Encrypted Disks, Virtual Disks, Folder Disks, Startup Manager, System Tweaker.
ExtraDisks is a suite of tools for creating Virtual disks on your computer - physical drives remain unchanged and are not divided into additional partitions. The program contains tools for creating Encrypted disks, Virtual disks based on files and Virtual disks based on folders. The current version consists of the following tools: Encrypted Disks, Virtual Disks, Folder Disks, Startup Manager, System Tweaker.
Windows | Shareware
Read More
ARMORTOOLS PROFESSIONAL 26.0.1
Security & Privacy :: Encryption Tools
 ArmorTools Professional is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
ArmorTools Professional is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
Windows | Shareware
Read More
System Utilities :: Text/Document Editors
Windows | Shareware
Read More
System Utilities :: Backup & Restore
 Back up your data and synchronize PCs, Macs, servers, and notebooks. The software comes with support for FTP, SSH, WebDAV, Amazon S3 and Glacier, Google Drive, OneDrive, Rackspace, Azure Storage, and many other cloud services. It includes ZIP compression, encryption, block-level copying, and a scheduler for automated backups. The scheduler can run as a service. Locked files can be copied. Includes Real Time Synchronization and Synthetic Backup.
Back up your data and synchronize PCs, Macs, servers, and notebooks. The software comes with support for FTP, SSH, WebDAV, Amazon S3 and Glacier, Google Drive, OneDrive, Rackspace, Azure Storage, and many other cloud services. It includes ZIP compression, encryption, block-level copying, and a scheduler for automated backups. The scheduler can run as a service. Locked files can be copied. Includes Real Time Synchronization and Synthetic Backup.
Windows | Shareware
Read More
System Utilities :: File Compression
 Who knew file compression could be so quick and easy? The world?s most popular zip utility, WinZip®, now includes 4 brand-new WinZip Pro apps that provide streamlined tools including a better PDF reader, image management, secure file backup, and expanded sharing. With a few simple clicks, our latest features allow you to combine and export files faster, add a watermark to your images, and keep a safe copy of your files in the Cloud.
Who knew file compression could be so quick and easy? The world?s most popular zip utility, WinZip®, now includes 4 brand-new WinZip Pro apps that provide streamlined tools including a better PDF reader, image management, secure file backup, and expanded sharing. With a few simple clicks, our latest features allow you to combine and export files faster, add a watermark to your images, and keep a safe copy of your files in the Cloud.
Windows | Shareware
Read More
Security & Privacy :: Encryption Tools
 A professional system for licensing and protecting executable files for Windows. The Enigma Protector is an essential tool for every developer of commercial software and shareware for Windows. The Enigma Protector includes a wide range of unique features aimed at protecting executable files from illegal copying, hacking, modification, and analysis. The supported formats include almost all types of 32- and 64-bit executable files.
A professional system for licensing and protecting executable files for Windows. The Enigma Protector is an essential tool for every developer of commercial software and shareware for Windows. The Enigma Protector includes a wide range of unique features aimed at protecting executable files from illegal copying, hacking, modification, and analysis. The supported formats include almost all types of 32- and 64-bit executable files.
Windows | Demo
Read More
USB DRIVE RECOVERY TOOL 8.1.5.5
System Utilities :: Backup & Restore
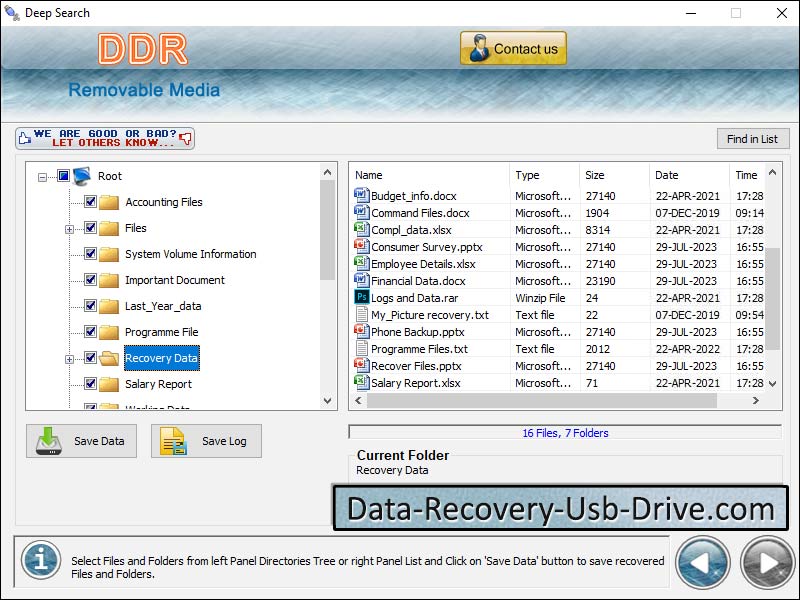 Website www.data-recovery-usb-drive.com offers file rescue tool to recover compressed or encrypted files missing due to corrupted portable removable USB media. Successful USB Drive Recovery tool salvages text and photographs of long file extension from pen drive media.
Website www.data-recovery-usb-drive.com offers file rescue tool to recover compressed or encrypted files missing due to corrupted portable removable USB media. Successful USB Drive Recovery tool salvages text and photographs of long file extension from pen drive media.
Windows | Shareware
Read More
FAT DATA RECOVERY SOFTWARE 8.1.4.8
System Utilities :: Backup & Restore
 Fat Data Recovery program enables users to restore folders, text that are missing or deleted due to crashed storage media usage. If you want to download file recovery tool then just check USB Drive Recovery to restore encrypted or lost data.
Fat Data Recovery program enables users to restore folders, text that are missing or deleted due to crashed storage media usage. If you want to download file recovery tool then just check USB Drive Recovery to restore encrypted or lost data.
Windows | Shareware
Read More
MEMORY CARD FILES RECOVERY SOFTWARE 8.1.5.6
System Utilities :: Backup & Restore
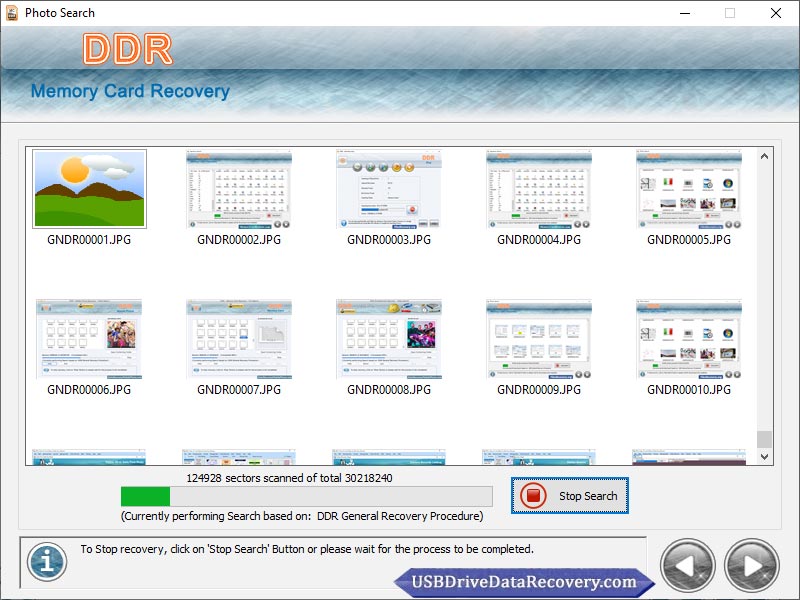 Freeware memory card data restoring application is available at www.usbdrivedatarecovery.com to retrieve images, audio and video clipping missing from digital camera. Memory Card Files Recovery Software is able to regain pictures lost due to forcefully shut down of system.
Freeware memory card data restoring application is available at www.usbdrivedatarecovery.com to retrieve images, audio and video clipping missing from digital camera. Memory Card Files Recovery Software is able to regain pictures lost due to forcefully shut down of system.
Windows | Shareware
Read More


