Search N5 Net Software Repository:
Search Files
Sponsor:
Browse:
- Audio & Multimedia (1596)
- Business (4238)
- Communications (1258)
- Desktop (183)
- Development (602)
- Education (171)
- Games & Entertainment (702)
- Graphic Apps (686)
- Home & Hobby (107)
- Network & Internet (571)
- Security & Privacy (532)
- Servers (65)
- System Utilities (11196)
- Web Development (284)
Areas Of Interest
Authors Area
Are you a software author? Take a look at our Author Resource Center where you will find marketing tools, software specifically created for promoting your software and a ton of other helpful resources.
CrococryptMirror Portable 1.43b
Security & Privacy :: Encryption Tools
CrococryptMirror is an encryption tool which mirrors complete folders to encrypted folders. The encryption algorithms that are used are AES and Twofish (256 bits, cascading). The keyfile is secured by a password using PKCS #5 (PBKDF2) with a SHA512/Whirlpool based HMAC using 100000 iterations and also AES and Twofish. Additionally, a ZIP compression for storage space optimization is used. For reasons of performance the synchronization of source and destination folder is done in the background. A backup copy of the keyfiles has to be stored at a secure place. Without the keyfile the containers cannot be decrypted. In the portable version of CrococryptMirror keyfile and settings are stored together with the application folder. Hence, the complete application can be transported on an external storage device. Moreover, the folder "container" can be used to store portable containers. Mirroring can be done manually (on-demand) or by using the sync service which detects directory changes on the fly. Features: Copying and synchronizing of files/folders/directories (recursive) to encrypted folders, Encryption of filenames, Source folders can be stored in multiple destination containers at the same time (e.g., USB disk drive and Cloud storage), Network drives can be used as sources and destinations, Explorer view to read encrypted containers. CrococryptMirror is a free software without registration, without activation, without limitations and without ads.
Specifications:
Version: 1.43b |
Download
|
Similar Products:
ARMORTOOLS PROFESSIONAL 26.2.1
Security & Privacy :: Encryption Tools
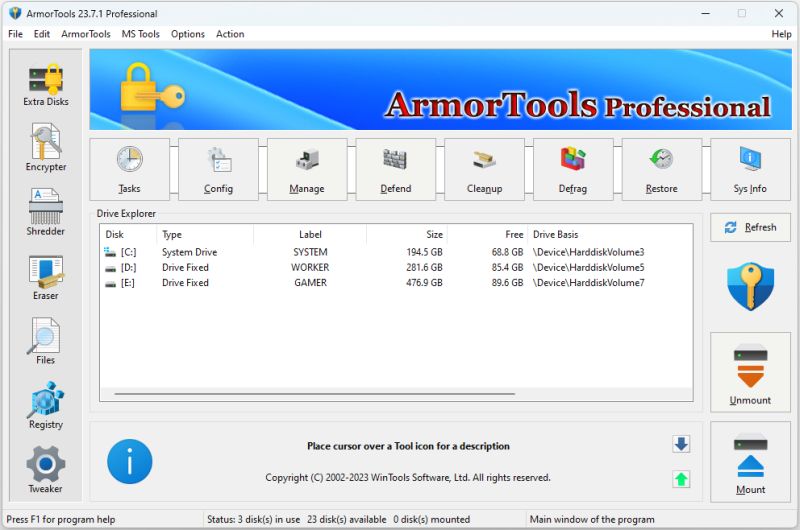 ArmorTools Professional is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
ArmorTools Professional is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
Windows | Shareware
Read More
Security & Privacy :: Encryption Tools
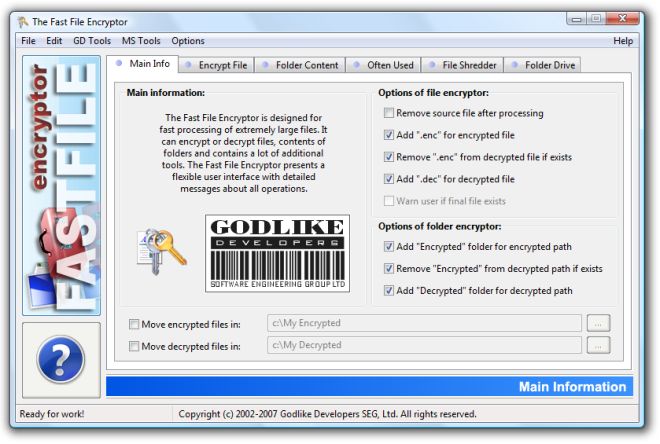 Fast File Encryptor is MS Windows compatible software designed for fast processing of extremely large files. It can encrypt and decrypt files, contents of folders using any file as a password. Fast File Encryptor contains a lot of additional tools and presents a flexible user interface with detailed messages about all operations. Fast File Encryptor compatible with ArmorTools software.
Fast File Encryptor is MS Windows compatible software designed for fast processing of extremely large files. It can encrypt and decrypt files, contents of folders using any file as a password. Fast File Encryptor contains a lot of additional tools and presents a flexible user interface with detailed messages about all operations. Fast File Encryptor compatible with ArmorTools software.
Windows | Shareware
Read More
Security & Privacy :: Encryption Tools
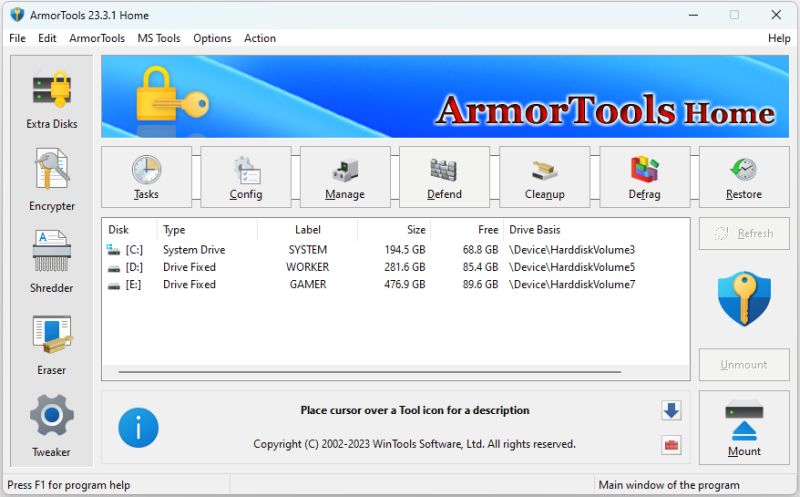 ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
Windows | Shareware
Read More
Security & Privacy :: Encryption Tools
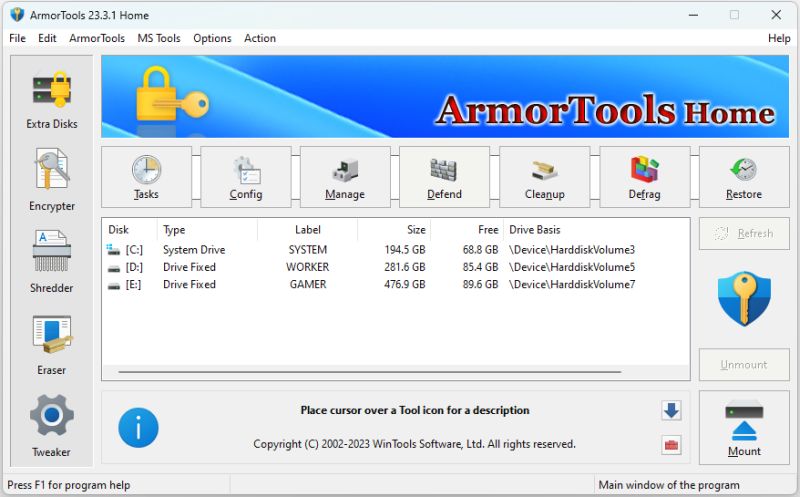 ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
Windows | Shareware
Read More




