Search N5 Net Software Repository:
Search Files
Sponsor:
Browse:
- Audio & Multimedia (1643)
- Business (3971)
- Communications (1197)
- Desktop (222)
- Development (607)
- Education (291)
- Games & Entertainment (731)
- Graphic Apps (698)
- Home & Hobby (108)
- Network & Internet (593)
- Security & Privacy (536)
- Servers (69)
- System Utilities (31267)
- Web Development (297)
Areas Of Interest
Authors Area
Are you a software author? Take a look at our Author Resource Center where you will find marketing tools, software specifically created for promoting your software and a ton of other helpful resources.
REFOG Personal Monitor 8.7.5.2850
Security & Privacy :: Covert Surveillance
Keystroke recording Once installed and running, Refog registers all keys pressed by a user, thus acting as a keylogger. This function captures all data that has been entered by your children or an employee using a keyboard, including chats, usernames, passwords, emails, search queries and other content. In addition to key logging, Refog is also able to log clipboard text. Screenshot history With customizable capability, Refog takes full color screenshots of a desktop screen. This ensures that the log of what is being typed by the user is backed up with visual evidence of exactly what they are doing. Without being monitored, it is often the case that employees get carried away with excessive web surfing, shopping and other personal tasks. With screenshot history, it is always possible to gather evidence if an employee is wasting the company's time. Multiple monitor configurations are supported! Application monitoring and file tracking Refog is able to record all programs executed on your PC, so it is possible to establish if your kid is playing games instead of doing his homework, an employee is wasting time offline (e.g. playing solitaire instead of working). In addition to programs, Refog stores all file operations (e.g. open, edit, copy, delete), and can reveal inappropriate interest in specific confidential documents. IM monitoring Refog is also compatible with all major instant messaging software (e.g. AIM, FacebookŪ,Yahoo! messenger, Skype, ICQ, Google Talk, MSN). It is not only able to log outgoing messages by a local user, but also incoming messages too. Email reports It is not necessary to gain physical access to monitored computers in order to view their logs. All reports can be delivered via email, and can be read anywhere. Invisible mode and password protection Web history logging
Specifications:
Version: 8.7.5.2850 |
Download
|
Similar Products:
Security & Privacy :: Covert Surveillance
 Stealth Keystroker is an undetectable keystroke logger (keylogger) which allows you to secretly record all activities of computer users and automatically deliver the logs to you via Email or FTP. Stealth Keystroker records all the system activities, such as email sent and received, websites visited, all keystrokes, passwords, chat convos, and takes screenshots at set intervals just like a surveillance camera. See more at www.key-stroke.com
Stealth Keystroker is an undetectable keystroke logger (keylogger) which allows you to secretly record all activities of computer users and automatically deliver the logs to you via Email or FTP. Stealth Keystroker records all the system activities, such as email sent and received, websites visited, all keystrokes, passwords, chat convos, and takes screenshots at set intervals just like a surveillance camera. See more at www.key-stroke.com
Windows | Shareware
Read More
EMPLOYEE MONITORING SOFTWARE REVIEW 1.1
Security & Privacy :: Covert Surveillance
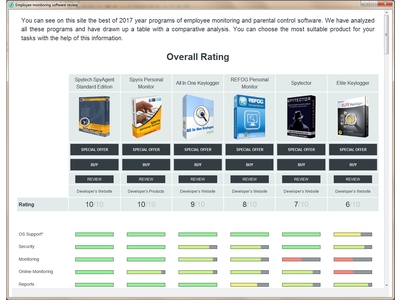 Employee monitoring software review is a comparative table of the best solutions for monitoring. All the programs were tested by our experts according to such criteria as OS Support, Security, Monitoring, Online Monitoring, Reports. Every criterion is represented by an extensive set of parameters, thus, practically all aspects of the software work are covered.
Employee monitoring software review is a comparative table of the best solutions for monitoring. All the programs were tested by our experts according to such criteria as OS Support, Security, Monitoring, Online Monitoring, Reports. Every criterion is represented by an extensive set of parameters, thus, practically all aspects of the software work are covered.
Windows | Freeware
Read More
Security & Privacy :: Covert Surveillance
 Keystroke Spy is an extremely powerful cost-effective alternative to our robust, all-in-one computer monitoring product - SpyAgent. Keystroke Spy, while being able to log all keystrokes typed by users without them knowing, can also be set to log keystrokes typed only in specific applications.
Keystroke Spy is an extremely powerful cost-effective alternative to our robust, all-in-one computer monitoring product - SpyAgent. Keystroke Spy, while being able to log all keystrokes typed by users without them knowing, can also be set to log keystrokes typed only in specific applications.
Windows | Shareware
Read More
PARENTAL CONTROL SOFTWARE REVIEW 1.1
Security & Privacy :: Covert Surveillance
 Parental control software are special programs parents use to monitor their children activity when they are online (wilfing) or offline (using available programs, playing games). These monitoring programs provide you with indispensable assistance to stop your children from surfing on inappropriate sites.
Parental control software are special programs parents use to monitor their children activity when they are online (wilfing) or offline (using available programs, playing games). These monitoring programs provide you with indispensable assistance to stop your children from surfing on inappropriate sites.
Windows | Freeware
Read More




