Search N5 Net Software Repository:
Search Files
Sponsor:
Browse:
- Audio & Multimedia (1565)
- Business (1732)
- Communications (466)
- Desktop (182)
- Development (569)
- Education (166)
- Games & Entertainment (707)
- Graphic Apps (683)
- Home & Hobby (105)
- Network & Internet (543)
- Security & Privacy (500)
- Servers (65)
- System Utilities (9315)
- Web Development (281)
Areas Of Interest
Authors Area
Are you a software author? Take a look at our Author Resource Center where you will find marketing tools, software specifically created for promoting your software and a ton of other helpful resources.
Ace Password Sniffer 1.4
New version provides candidates of username or password for HTTP post submission. The most powerful and effetive password sniffer. Ace Password Sniffer can listen on your LAN and enable network administrators or parents to capture passwords of any network user. Currently Ace Password Sniffer can monitor and capture passwords through FTP, POP3, HTTP, SMTP, Telnet, and etc. Ace Password Sniffer works passively and don't generate any network traffic, therefore, it is very hard to be detected by others. And you needn't install any additional software on other PCs or workstations. If your network is connected through switch, you can run the sniffer on the gateway or proxy server, which can get all network traffic. This stealth-monitoring utility is useful to recover your network passwords, to receive network passwords of children for parents, and to monitor passwords abuse for server administrators. Features: * Efficient You can see the passwords as soon as it appeared on LAN. * Support Various Protocols Fully support application protocols of FTP, SMTP, POP3, TELNET, etc. That means user names and passwords used to send and receive emails, to log on a web site, or to log on a server, can all be captured and saved. * Support HTTP Protocol Support HTTP protocol, including proxy password, basic http authenticate authoriation and most passwords submitted through HTML, no matter they are encoded by MIME or base64. * Verify whether the captured passwords are valid It can tell whether the passwords are right. You can even get the replies from the server for the login. And it always keeps trying to get valid user name and password pairs.
Specifications:
Version: 1.4 |
Download
|
Similar Products:
Security & Privacy :: Other
 Privacy Eraser is an all-in-one privacy suite, PC optimization and cleaning tool. It cleans all of your internet history traces and past activities with one click, recovers hard drive space by deleting unnecessary and redundant files, speeds up internet surfing and browsing, boosts your PC's performance and stability making it faster, secure and more efficient.
Privacy Eraser is an all-in-one privacy suite, PC optimization and cleaning tool. It cleans all of your internet history traces and past activities with one click, recovers hard drive space by deleting unnecessary and redundant files, speeds up internet surfing and browsing, boosts your PC's performance and stability making it faster, secure and more efficient.
Windows | Freeware
Read More
Security & Privacy :: Other
 Privacy Eraser is an all-in-one privacy suite, PC optimization and cleaning tool. It cleans all of your internet history traces and past activities with one click, recovers hard drive space by deleting unnecessary and redundant files, speeds up internet surfing and browsing, boosts your PC's performance and stability making it faster, secure and more efficient.
Privacy Eraser is an all-in-one privacy suite, PC optimization and cleaning tool. It cleans all of your internet history traces and past activities with one click, recovers hard drive space by deleting unnecessary and redundant files, speeds up internet surfing and browsing, boosts your PC's performance and stability making it faster, secure and more efficient.
Windows | Freeware
Read More
PASSWORD SECURITY SCANNER 1.65
Security & Privacy :: Other
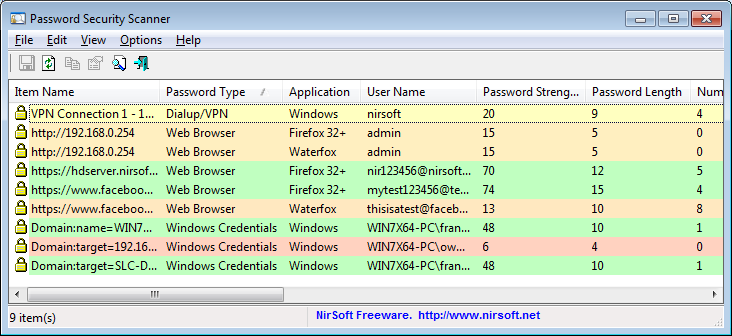 This utility scans the passwords stored by popular Windows applications (Microsoft Outlook, Internet Explorer, Mozilla Firefox, and more...) and displays security information about all these passwords. The security information of every stored password includes the total number of characters, number of numeric characters, number of lowercase/uppercase characters, number of repeating characters, and password strength.
This utility scans the passwords stored by popular Windows applications (Microsoft Outlook, Internet Explorer, Mozilla Firefox, and more...) and displays security information about all these passwords. The security information of every stored password includes the total number of characters, number of numeric characters, number of lowercase/uppercase characters, number of repeating characters, and password strength.
Windows | Freeware
Read More
Security & Privacy :: Other
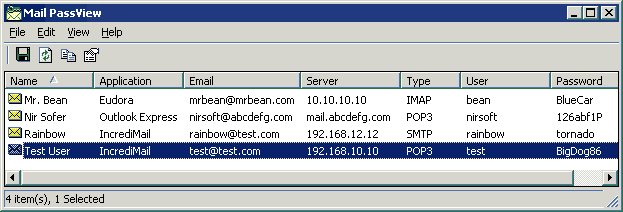 Mail PassView is a small password-recovery tool that reveals the passwords and other account details for the following email clients:
Outlook Express
Microsoft Outlook 2000 (POP3 and SMTP Accounts only)
Microsoft Outlook 2002/2003 (POP3, IMAP, HTTP and SMTP Accounts)
IncrediMail
Eudora
Netscape 6.x/7.x
Mozilla Thunderbird
Group Mail Free
Web-based email clients
Mail PassView is a small password-recovery tool that reveals the passwords and other account details for the following email clients:
Outlook Express
Microsoft Outlook 2000 (POP3 and SMTP Accounts only)
Microsoft Outlook 2002/2003 (POP3, IMAP, HTTP and SMTP Accounts)
IncrediMail
Eudora
Netscape 6.x/7.x
Mozilla Thunderbird
Group Mail Free
Web-based email clients
Windows | Freeware
Read More




