Search N5 Net Software Repository:
Search Files
Sponsor:
Browse:
- Audio & Multimedia (1596)
- Business (4238)
- Communications (1258)
- Desktop (183)
- Development (602)
- Education (171)
- Games & Entertainment (702)
- Graphic Apps (686)
- Home & Hobby (107)
- Network & Internet (571)
- Security & Privacy (532)
- Servers (65)
- System Utilities (11196)
- Web Development (284)
Areas Of Interest
Authors Area
Are you a software author? Take a look at our Author Resource Center where you will find marketing tools, software specifically created for promoting your software and a ton of other helpful resources.
TotalRecall 1.1
A lot of different information about a user's activity is kept within the personal computer. Usually the user does not know about its existence. TotalRecall is a free forensic analysis tool to reconstruct Microsoft Internet Explorer (MS IE) activity and some user's activity on the computer. IE caches URLs which were visited by users. MS IE stores its Internet activity in index.dat files. These files are binary database files, which are used by Microsoft as the file type for storing several different sets of information. Included among these files are user data, Internet cookies, and Internet history storage. These files are found scattered throughout the users' profile folders. Because browser activity files are in binary form, special tools are required to read them. Now, our program investigates: IE activity, IE history, IE cookie, IE favorites and user's activity (recent files and folders, not erased temporary files). After processing, the information from the source is loaded into the appropriate table (all information for the current user may be completed automatically). It is possible to open the file by the program with which it is associated just by double clicking on a selected line of a table. When you select the image from the table its thumbnail is shown at the bottom right corner and it helps you preview the pictures using a built-in viewer. Any table may be sorted by columns in any order. Find-command locates the row of a table containing the regular occurrence of the search string. The table context menu provides quick access to useful commands (Open, Open with?, Open Folder, Copy/Move to?, etc.). The contents of any table may be exported to an .XML or a .TXT file. The program allows collecting data for all tables or for some tables depending upon the criteria set. The program determines the language of your installation of Windows and sets the working language in accordance with corresponding language file (if it exists) then sets it as default.
Specifications:
Version: 1.1 |
Download
|
Similar Products:
Security & Privacy :: Other
 Privacy Eraser is an all-in-one privacy suite, PC optimization and cleaning tool. It cleans all of your internet history traces and past activities with one click, recovers hard drive space by deleting unnecessary and redundant files, speeds up internet surfing and browsing, boosts your PC's performance and stability making it faster, secure and more efficient.
Privacy Eraser is an all-in-one privacy suite, PC optimization and cleaning tool. It cleans all of your internet history traces and past activities with one click, recovers hard drive space by deleting unnecessary and redundant files, speeds up internet surfing and browsing, boosts your PC's performance and stability making it faster, secure and more efficient.
Windows | Freeware
Read More
Security & Privacy :: Other
 Privacy Eraser is an all-in-one privacy suite, PC optimization and cleaning tool. It cleans all of your internet history traces and past activities with one click, recovers hard drive space by deleting unnecessary and redundant files, speeds up internet surfing and browsing, boosts your PC's performance and stability making it faster, secure and more efficient.
Privacy Eraser is an all-in-one privacy suite, PC optimization and cleaning tool. It cleans all of your internet history traces and past activities with one click, recovers hard drive space by deleting unnecessary and redundant files, speeds up internet surfing and browsing, boosts your PC's performance and stability making it faster, secure and more efficient.
Windows | Freeware
Read More
PASSWORD SECURITY SCANNER 1.65
Security & Privacy :: Other
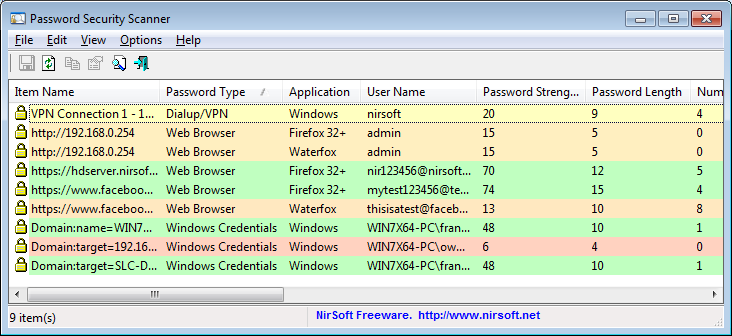 This utility scans the passwords stored by popular Windows applications (Microsoft Outlook, Internet Explorer, Mozilla Firefox, and more...) and displays security information about all these passwords. The security information of every stored password includes the total number of characters, number of numeric characters, number of lowercase/uppercase characters, number of repeating characters, and password strength.
This utility scans the passwords stored by popular Windows applications (Microsoft Outlook, Internet Explorer, Mozilla Firefox, and more...) and displays security information about all these passwords. The security information of every stored password includes the total number of characters, number of numeric characters, number of lowercase/uppercase characters, number of repeating characters, and password strength.
Windows | Freeware
Read More
Security & Privacy :: Other
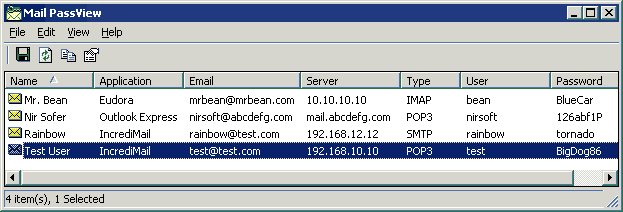 Mail PassView is a small password-recovery tool that reveals the passwords and other account details for the following email clients:
Outlook Express
Microsoft Outlook 2000 (POP3 and SMTP Accounts only)
Microsoft Outlook 2002/2003 (POP3, IMAP, HTTP and SMTP Accounts)
IncrediMail
Eudora
Netscape 6.x/7.x
Mozilla Thunderbird
Group Mail Free
Web-based email clients
Mail PassView is a small password-recovery tool that reveals the passwords and other account details for the following email clients:
Outlook Express
Microsoft Outlook 2000 (POP3 and SMTP Accounts only)
Microsoft Outlook 2002/2003 (POP3, IMAP, HTTP and SMTP Accounts)
IncrediMail
Eudora
Netscape 6.x/7.x
Mozilla Thunderbird
Group Mail Free
Web-based email clients
Windows | Freeware
Read More




