Search N5 Net Software Repository:
Search Files
Sponsor:
Browse:
- Audio & Multimedia (1565)
- Business (1732)
- Communications (466)
- Desktop (182)
- Development (569)
- Education (166)
- Games & Entertainment (707)
- Graphic Apps (683)
- Home & Hobby (105)
- Network & Internet (543)
- Security & Privacy (500)
- Servers (65)
- System Utilities (9315)
- Web Development (281)
Areas Of Interest
Authors Area
Are you a software author? Take a look at our Author Resource Center where you will find marketing tools, software specifically created for promoting your software and a ton of other helpful resources.
Insider 3.02
Security & Privacy :: Encryption Tools
Everybody has a right to privacy. Your confidential information can be saved as a file (photo, document, program, music or video file etc.). You do not want anyone to know your secret and anyone to suspect you have a secret. Insider allows the user to conceal details (of their private life or business) from unauthorized viewers. If the user needs to conceal confidential files, he can use various programs for protection. Meanwhile these programs do not allow use of the concealed data as easily and safely as you can with normally unprotected files. Our program is not available obviously. It is hidden inside another, absolutely inconspicious program (file compression utility). Confidential files are compressed and kept inside containers - usually pictures. These pictures themselves are not distorted. Any program that can be used to view the pictures will show the container's content only. The above mentioned features are very important psychologically. When there is no indication of an encrypted file, encryption program or special encryption tools are not evident, the computer's owner is above of suspicion. As a result nobody will try to reveal their confidential information. Insider creates compressed archives and works with these files while the archives themselves are not evident on the user?s computer. To encrypt a compressed archive before hiding it, the latest strong cryptography methods known are used. The size of a hidden file is not limited. If you know the right password, the hidden archive can be viewed and processed very easily. If this program had deleted the file they could not be restored. Any special software or hardware is powerless to restore them. This program may be used for information exchange via Internet. Hidden archives may be sent via e-mail or published on web sites. You may also send the photos (with hidden files) via mobile operators.The containers may be kept within mobile phones or digital cameras where they will look like usual photos.
Specifications:
Version: 3.02 |
Download
|
Similar Products:
BATCH FILE ENCRYPT FREE 5.0.135
Security & Privacy :: Encryption Tools
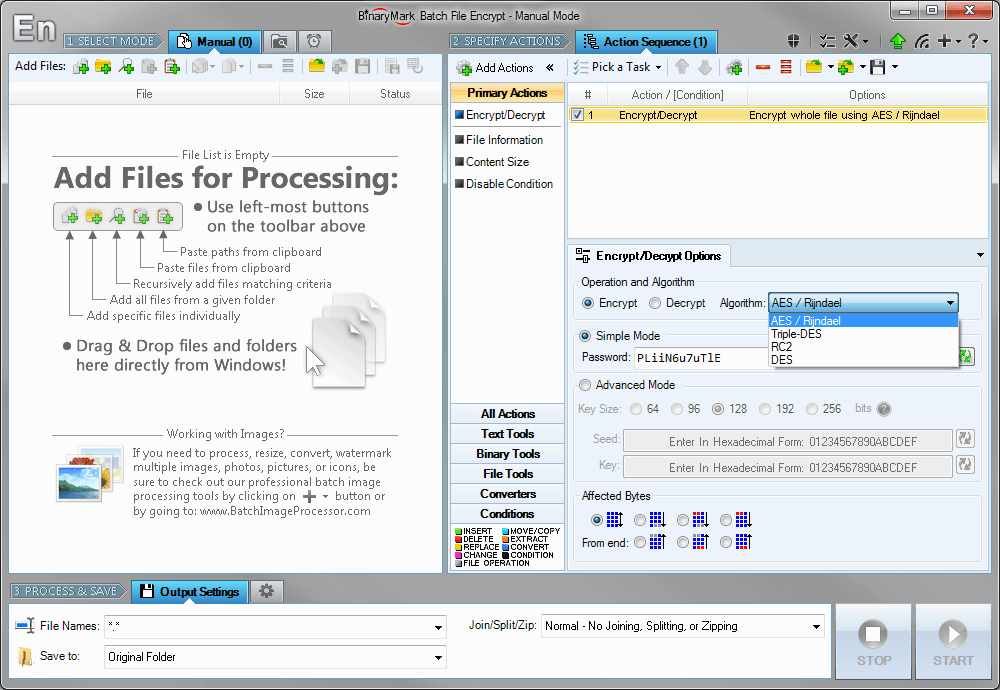 Encrypt and decrypt whole files or their parts using AES, Triple-DES (3DES), RC2, and DES symmetric algorithms. You can encrypt files with a single password or specify cryptographic keys (vectors) instead. You can change key bit length for better protection. You can select specifically which bytes in a file should be encrypted/decrypted, though by default the whole file is processed.
Encrypt and decrypt whole files or their parts using AES, Triple-DES (3DES), RC2, and DES symmetric algorithms. You can encrypt files with a single password or specify cryptographic keys (vectors) instead. You can change key bit length for better protection. You can select specifically which bytes in a file should be encrypted/decrypted, though by default the whole file is processed.
Windows | Shareware
Read More
ARMORTOOLS PROFESSIONAL 26.2.1
Security & Privacy :: Encryption Tools
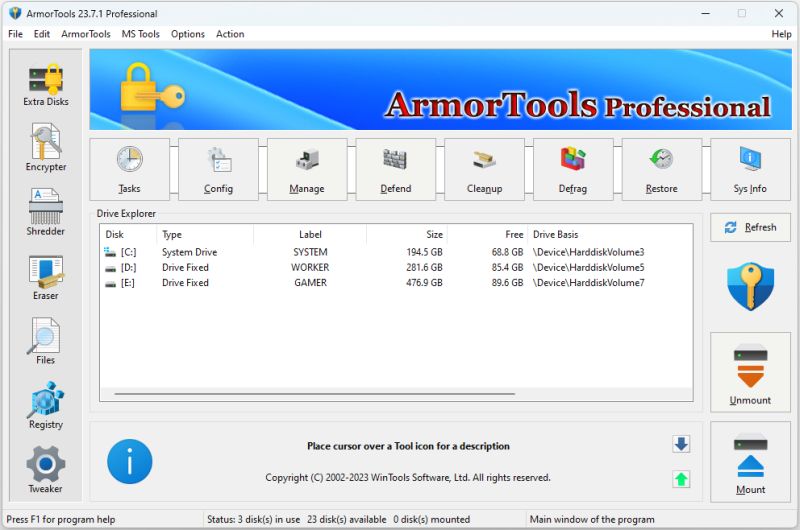 ArmorTools Professional is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
ArmorTools Professional is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
Windows | Shareware
Read More
Security & Privacy :: Encryption Tools
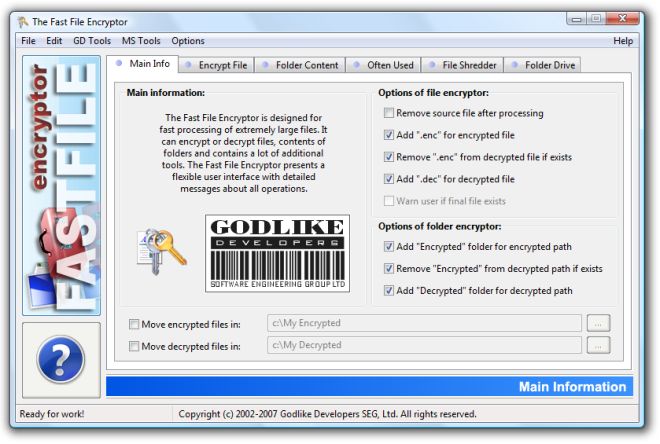 Fast File Encryptor is MS Windows compatible software designed for fast processing of extremely large files. It can encrypt and decrypt files, contents of folders using any file as a password. Fast File Encryptor contains a lot of additional tools and presents a flexible user interface with detailed messages about all operations. Fast File Encryptor compatible with ArmorTools software.
Fast File Encryptor is MS Windows compatible software designed for fast processing of extremely large files. It can encrypt and decrypt files, contents of folders using any file as a password. Fast File Encryptor contains a lot of additional tools and presents a flexible user interface with detailed messages about all operations. Fast File Encryptor compatible with ArmorTools software.
Windows | Shareware
Read More
Security & Privacy :: Encryption Tools
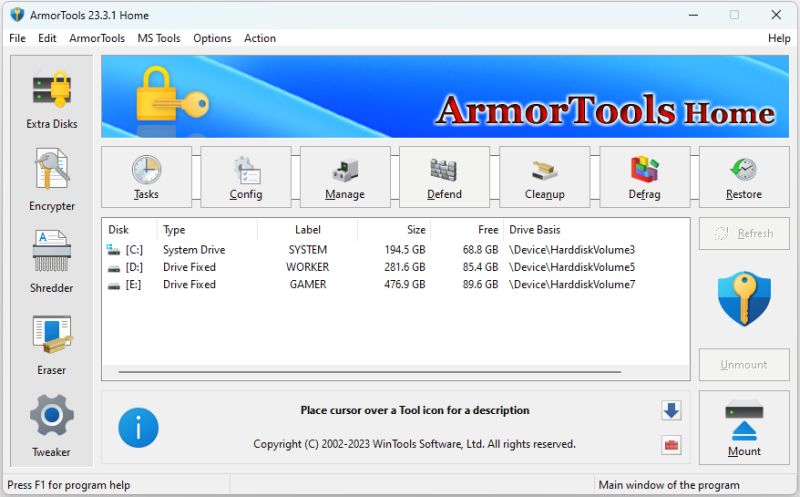 ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
Windows | Shareware
Read More




