Search N5 Net Software Repository:
Search Files
Sponsor:
Browse:
- Audio & Multimedia (1596)
- Business (4238)
- Communications (1258)
- Desktop (183)
- Development (602)
- Education (171)
- Games & Entertainment (702)
- Graphic Apps (686)
- Home & Hobby (107)
- Network & Internet (571)
- Security & Privacy (532)
- Servers (65)
- System Utilities (11196)
- Web Development (284)
Areas Of Interest
Authors Area
Are you a software author? Take a look at our Author Resource Center where you will find marketing tools, software specifically created for promoting your software and a ton of other helpful resources.
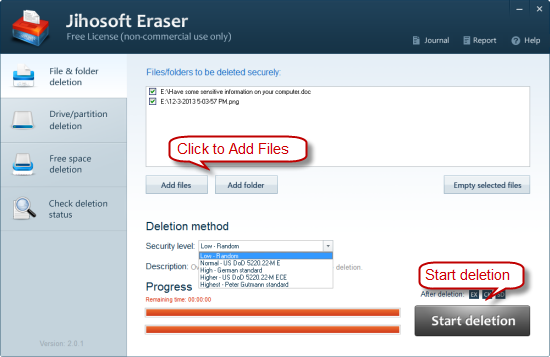
Jihosoft Free Eraser 2.0
Security & Privacy :: Encryption Tools
Have some sensitive information on your computer and worry about the data leakage one day? Now with Jihosoft Eraser, you can permanently remove sensitive data from your hard drive by overwriting it several times with carefully selected patterns. Key Features of Jihosoft Eraser - Delete sensitive files and folders from targeted path - Shred an entire drive or partition securely - Completely erase files on the unused space and slack space on a drive - 5 advanced data erasure patterns keep your data safe How Jihosoft Eraser will Help you When you delete files and then empty the Recycle Bin, you don't actually erase the information, you just delete the reference to it so the operating system can't find it. All the data is still there and, unless it's overwritten, can be easily recovered using file recovery software. Jihosoft Eraser just help you securely remove data and make them unrecoverable anymore with 5 data erasure patterns. Flexible Data Wipe Methods Altogether there are 3 data wipe methods available for you to choose: File & folder deletion, Drive/partition deletion, and Free space deletion. You can choose the one meets your demands best. Five Advanced Data Destruction Patterns Erase your sensitive information with 5 carefully selected data destruction patterns, keep a high security of the deleted files: Low - Random, Normal - US DoD 5220.22-ME, High - German standard, Higher - US DoD 5220.22-M ECE, and Highest - Peter Gutmann standard. Easy-to-use and 100% Clean With straight forward product user interface, you can master the utility even if you are a computer beginner. It doesn't contain any malware, and will do no harm to your PC or external storage devices.
Specifications:
Version: 2.0 |
Download
|
Similar Products:
ARMORTOOLS PROFESSIONAL 26.2.1
Security & Privacy :: Encryption Tools
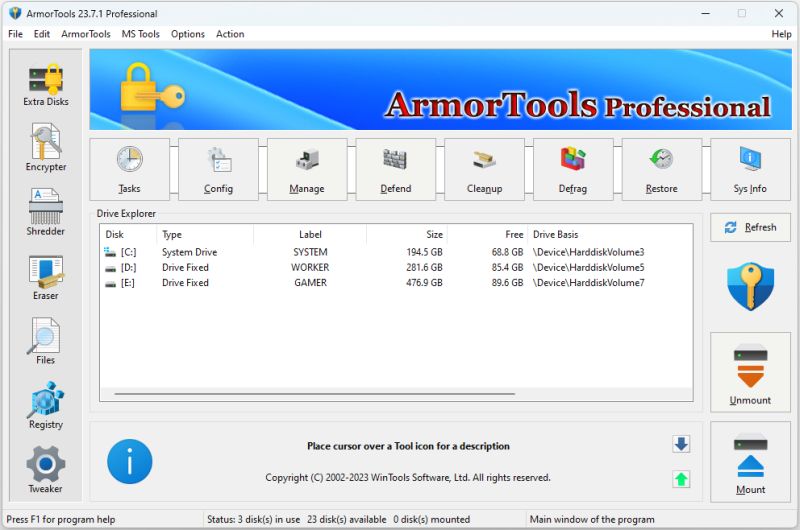 ArmorTools Professional is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
ArmorTools Professional is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
Windows | Shareware
Read More
Security & Privacy :: Encryption Tools
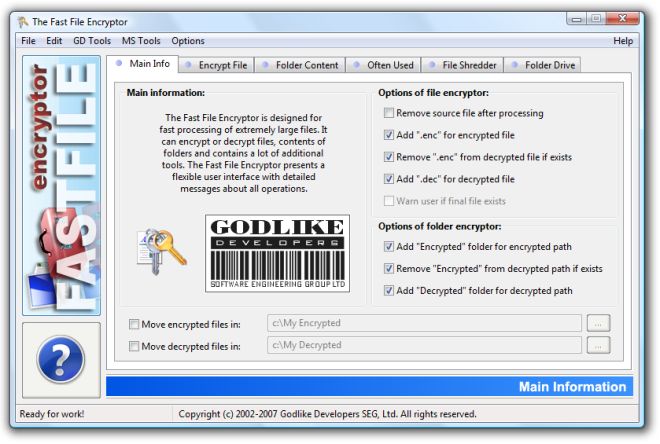 Fast File Encryptor is MS Windows compatible software designed for fast processing of extremely large files. It can encrypt and decrypt files, contents of folders using any file as a password. Fast File Encryptor contains a lot of additional tools and presents a flexible user interface with detailed messages about all operations. Fast File Encryptor compatible with ArmorTools software.
Fast File Encryptor is MS Windows compatible software designed for fast processing of extremely large files. It can encrypt and decrypt files, contents of folders using any file as a password. Fast File Encryptor contains a lot of additional tools and presents a flexible user interface with detailed messages about all operations. Fast File Encryptor compatible with ArmorTools software.
Windows | Shareware
Read More
Security & Privacy :: Encryption Tools
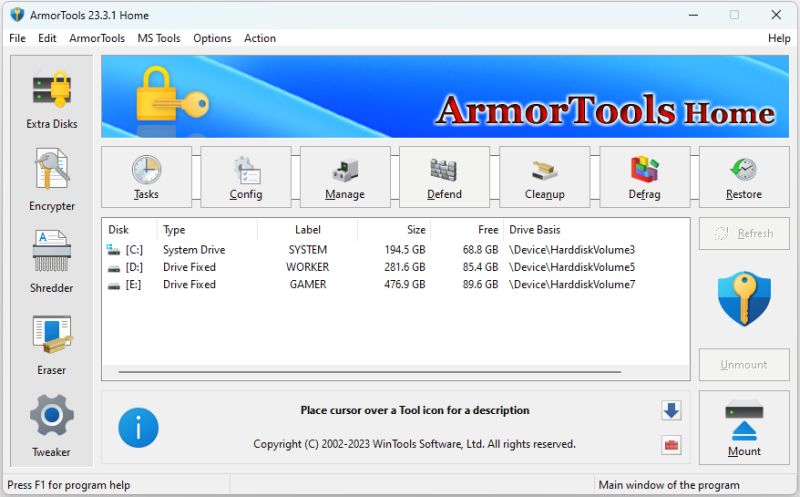 ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
Windows | Shareware
Read More
Security & Privacy :: Encryption Tools
 ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
Windows | Shareware
Read More