Search N5 Net Software Repository:
Search Files
Sponsor:
Browse:
- Audio & Multimedia (1643)
- Business (3971)
- Communications (1197)
- Desktop (222)
- Development (607)
- Education (291)
- Games & Entertainment (731)
- Graphic Apps (698)
- Home & Hobby (108)
- Network & Internet (593)
- Security & Privacy (536)
- Servers (69)
- System Utilities (31267)
- Web Development (297)
Areas Of Interest
Authors Area
Are you a software author? Take a look at our Author Resource Center where you will find marketing tools, software specifically created for promoting your software and a ton of other helpful resources.
Activity and Authentication Analyzer 1.64.0.10
Security & Privacy :: Access Control
Your PC keeps records of both your online and off-line activity. Any of the Web Pages, Movies, Pictures, Sounds, E-mail and Everything Else you have ever viewed could easily be recovered - even after many years passed! This is a serious threat to the legitimate user's privacy. Activity and Authentication Analyzer is a solution to this problem. AAAnalyzer is the powerful security software, which has been primarily destined to comprehensive search, analysis, the user activity traces left after work. The activity analysis and authentication or how it is called in brief ?statistics?, as the method of information (intelligence data) collection is applied either for the preliminary exploring or when the access to information (posted message, telephone talk) is impossible or unwanted. As applied to the computer security topics the activity analysis and authentication is performed when it is impossible to get documents? copies, which user worked on, for example, stored either on ciphered or dismounted disk containers. Nevertheless, ?nothing is disappeared without any trace? and it is possible, therefore, to disclose much useful data from the documents? names, Internet addresses, which were visited, the applications? names which were launched or file names which were searched, last user?s logon name. Windows 95/98/NT/2000/XP/2003/Vista/7/8/8.1/10/11 has the system registry database, which is useful, for the first, to the very OS, but, for the second, for keeping many traces (evidences in other words) left by routine work and for either exploration, or for reconstruction of user?s activity. Its built-in functionality allows to search the traces left in system registry, stored in registry keys related to the activity and authentication analysis
Specifications:
Version: 1.64.0.10 |
Download
|
Similar Products:
Security & Privacy :: Access Control
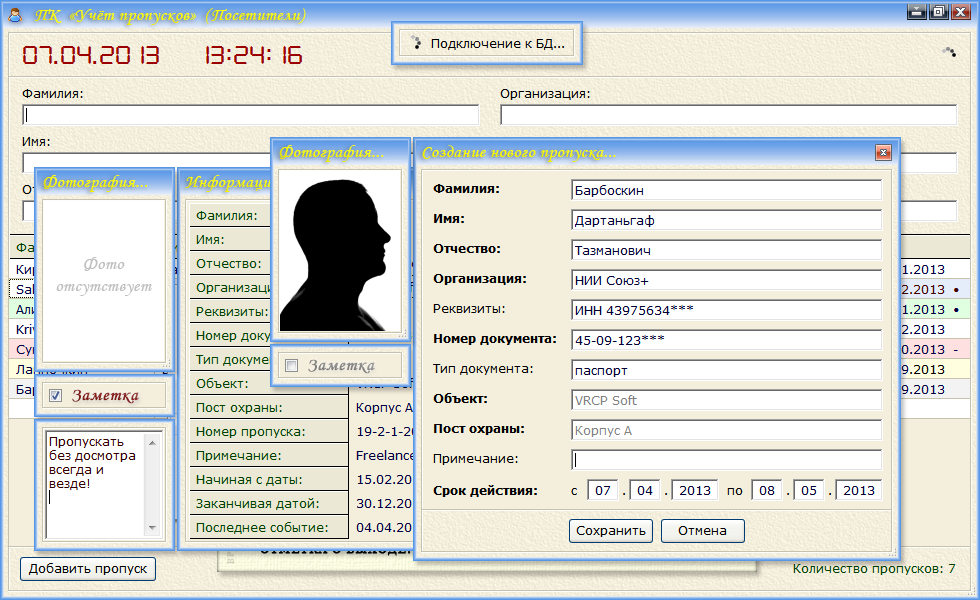 The program complex 'Accounting of Admissions' is intended for the organization of the automated work with the electronic database containing information on admissions (constant, temporary or single) on the protected objects for the purpose of implementation of additional control of the entering/leaving persons, and also the driving/leaving motor transport.
The program complex 'Accounting of Admissions' is intended for the organization of the automated work with the electronic database containing information on admissions (constant, temporary or single) on the protected objects for the purpose of implementation of additional control of the entering/leaving persons, and also the driving/leaving motor transport.
Windows | Freeware
Read More
SCHOOL TRACK STUDENT ATTENDANCE SOFTWARE 6.6
Security & Privacy :: Access Control
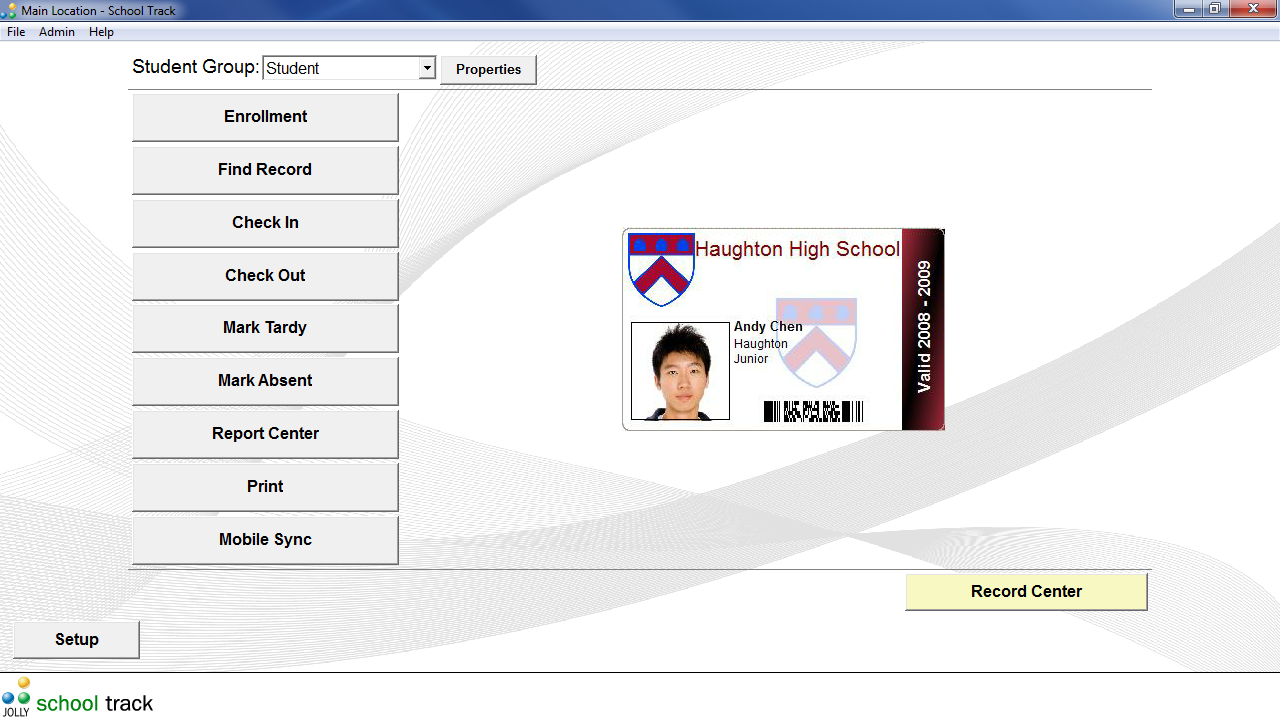 Track student attendance and tardiness, issue tardy slips and hall passes, assign warnings and detention. Parents can receive e-mail notification of any infraction occurred.
Track student attendance and tardiness, issue tardy slips and hall passes, assign warnings and detention. Parents can receive e-mail notification of any infraction occurred.
Windows | Demo
Read More
LOBBY TRACK FREE VISITOR MANAGEMENT SOFTWARE 6.7
Security & Privacy :: Access Control
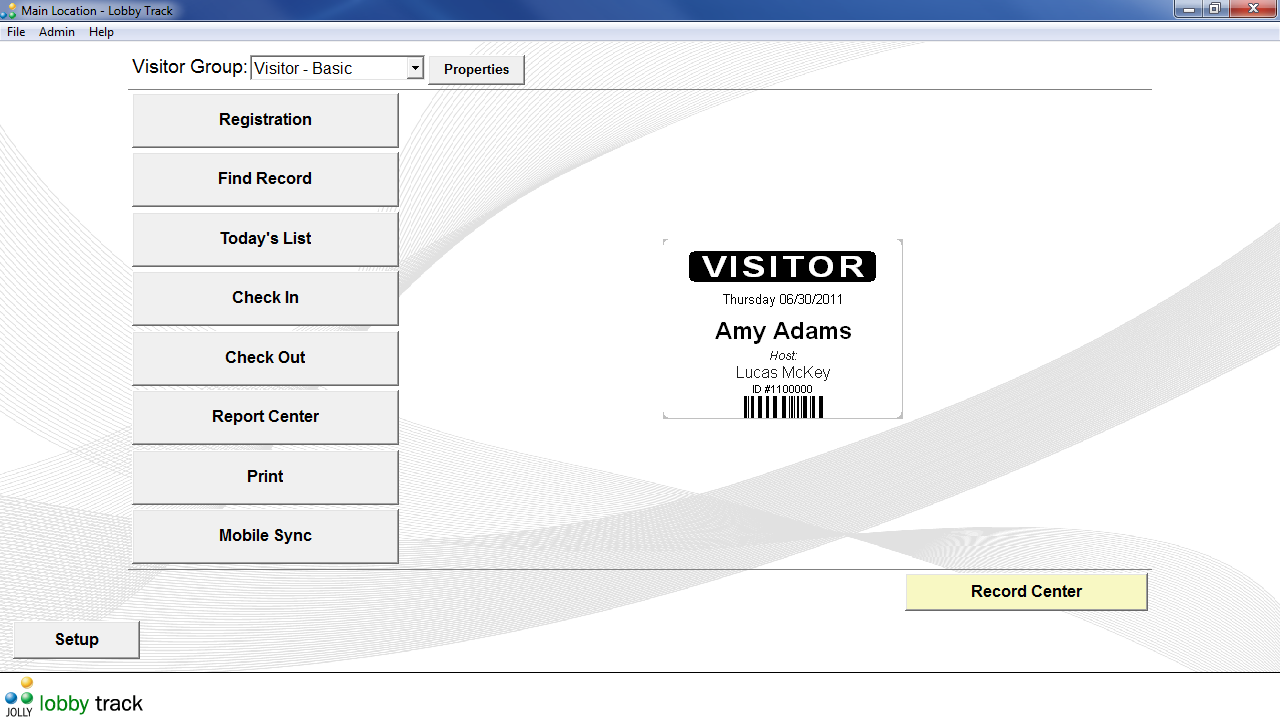 Pre-register visitors in advance or register them as they arrive. Issue professional visitor badges on visitor arrival.
Pre-register visitors in advance or register them as they arrive. Issue professional visitor badges on visitor arrival.
Windows | Freeware
Read More
PASSWORD GENERATOR TRIAL 3.0.119
Security & Privacy :: Access Control
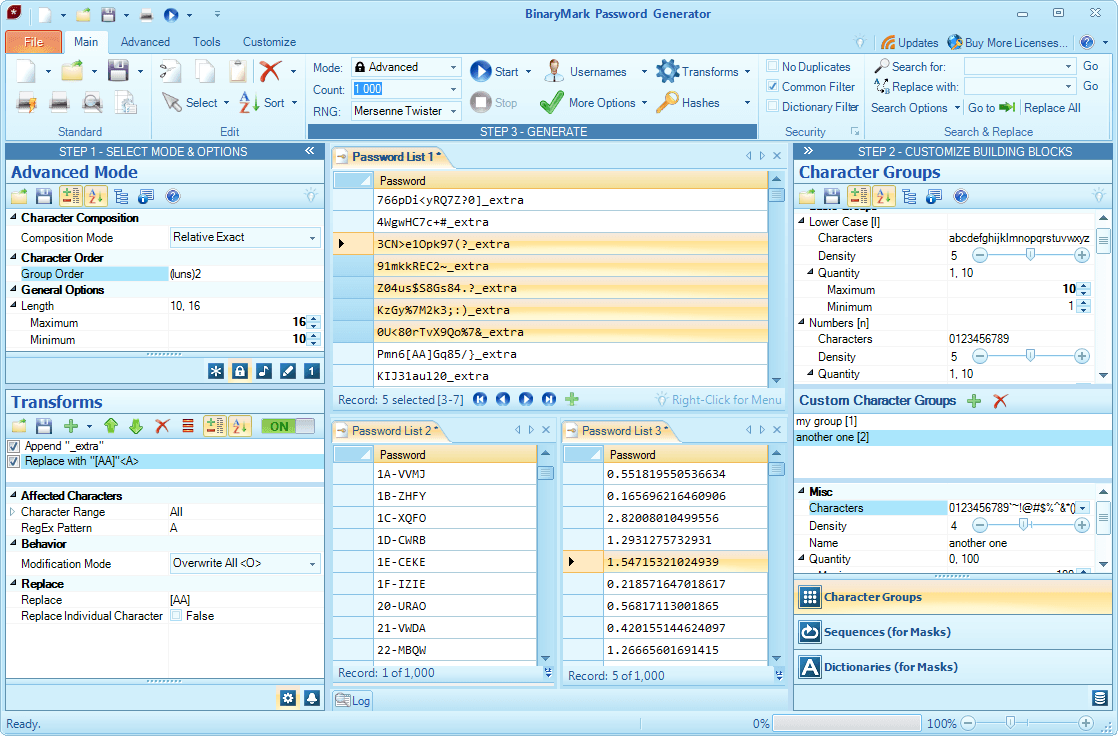 Easily generate millions of unique strong random passwords, numbers, masked codes, pronounceable passwords, usernames, and more. Control character placement, composition, and frequency of occurrence. Allow or disallow duplicate, consecutive, repeating, and similar characters. Use words, sequential parts, random numbers, and non-ASCII Unicode characters in generation. Avoid weak passwords using filters. Save results to Excel, file, or database.
Easily generate millions of unique strong random passwords, numbers, masked codes, pronounceable passwords, usernames, and more. Control character placement, composition, and frequency of occurrence. Allow or disallow duplicate, consecutive, repeating, and similar characters. Use words, sequential parts, random numbers, and non-ASCII Unicode characters in generation. Avoid weak passwords using filters. Save results to Excel, file, or database.
Windows | Commercial
Read More




