Search N5 Net Software Repository:
Search Files
Sponsor:
Browse:
- Audio & Multimedia (1643)
- Business (3971)
- Communications (1197)
- Desktop (222)
- Development (607)
- Education (291)
- Games & Entertainment (731)
- Graphic Apps (698)
- Home & Hobby (108)
- Network & Internet (593)
- Security & Privacy (536)
- Servers (69)
- System Utilities (31267)
- Web Development (297)
Areas Of Interest
Authors Area
Are you a software author? Take a look at our Author Resource Center where you will find marketing tools, software specifically created for promoting your software and a ton of other helpful resources.
wodSSHServer 2.5.4
wodSSHServer is an SSH Server ActiveX component (but also Telnet Server ActiveX as well) that will give you ability to easily add SSH2 (and SFTP) server capabilities to your application, as well as old TELNET server protocol. SSH protocol provides strong encryption of data, and authentication of users over insecure networks, such as Internet. Using it is really easy. Add it to your form (or create instance on the fly), use internal methods to generate pair of keys for the server (or import existing ones from other SSH servers) and start the server. From that moment, clients will be able to connect to your server, and do the following: enter chat that you created for them, start command prompt and execute commands inside (just as they would do it from the console window), start some program of their choice use internally provided SFTP (secure ftp) server, or open port forwarding for other programs All of this, of course, can be adjusted by your needs. By default, server will not allow anyone to login unless you specify so (using LoginPassword event that is fired when someone wants to login to your server). Once connected, you will get the information about service type user requests. At this point, you can accept, reject or even change the service he requested. Or, you can just leave him alone and not interfere with his actions at all. Using wodSSHServer is ideal if you need server side of encrypted communication, and don't want to hassle with certificates (used in SSL communication). Almost everyone today has some sort of SSH client which can be used to connect to your server. Included samples will show you, step by step, how to manually respond to client's actions. You can make an interface that will talk to the clients (like an BBS system), they will enter commands and different type of values in your program where you can evaluate them. This is ideal for making restricted access area where users will be allowed only to, login and change passwords
Specifications:
Version: 2.5.4 |
Download
|
Similar Products:
SCARDX EASY SMART CARD ACTIVEX CONTROL 2.1
Development :: Active X
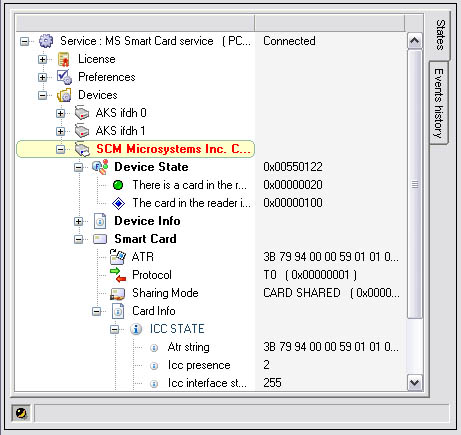 SCardX Easy is a standart ActiveX control which creates the communication channel between your application or web site and an opened smart card.
Supports any of PC/SC compatible card readers and USB tokens and any of ISO-7816 compatible smart cards like GSM SIM cards, EMV payment cards, identity and cryptographic cards and all other types of processor cards.
Add smart cards to your web site or to your application easily!
SCardX Easy is a standart ActiveX control which creates the communication channel between your application or web site and an opened smart card.
Supports any of PC/SC compatible card readers and USB tokens and any of ISO-7816 compatible smart cards like GSM SIM cards, EMV payment cards, identity and cryptographic cards and all other types of processor cards.
Add smart cards to your web site or to your application easily!
Windows | Shareware
Read More
EDRAW VIEWER COMPONENT FOR EXCEL 8.0.0.733
Development :: Active X
 Edraw Viewer Component for Excel contains a standard ActiveX control that acts as an ActiveX document container for hosting MS Excel documents in a custom form or Web page.
Edraw Viewer Component for Excel contains a standard ActiveX control that acts as an ActiveX document container for hosting MS Excel documents in a custom form or Web page.
Windows | Shareware
Read More
Development :: Active X
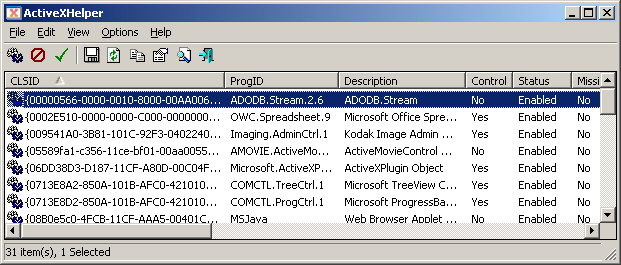 ActiveXHelper is a small utility that allows you to view essential information about ActiveX components installed on your computer. You can view the entire (and very large !) list of ActiveX components by loading it from HKEY_CLASSES_ROOT\CLSID Registry key, or alternatively, display only the ActiveX components that you specify.
ActiveXHelper is a small utility that allows you to view essential information about ActiveX components installed on your computer. You can view the entire (and very large !) list of ActiveX components by loading it from HKEY_CLASSES_ROOT\CLSID Registry key, or alternatively, display only the ActiveX components that you specify.
Windows | Freeware
Read More
EDRAW FLOWCHART ACTIVEX CONTROL 2.3
Development :: Active X
 Do you want to learn how to draw? Now you can online! Learn how to draw like an local application with EDraw ActiveX Control, that lets you quickly build basic flowcharts, organizational charts, business charts, hr diagram, work flowchart, programming flowchart and network diagrams. It is a MFC based ActiveX control, compiled with Microsoft VC++ 6.0!
Do you want to learn how to draw? Now you can online! Learn how to draw like an local application with EDraw ActiveX Control, that lets you quickly build basic flowcharts, organizational charts, business charts, hr diagram, work flowchart, programming flowchart and network diagrams. It is a MFC based ActiveX control, compiled with Microsoft VC++ 6.0!
Windows | Shareware
Read More




