Search N5 Net Software Repository:
Search Files
Sponsor:
Browse:
- Audio & Multimedia (1565)
- Business (1732)
- Communications (466)
- Desktop (182)
- Development (569)
- Education (166)
- Games & Entertainment (707)
- Graphic Apps (683)
- Home & Hobby (105)
- Network & Internet (543)
- Security & Privacy (500)
- Servers (65)
- System Utilities (9315)
- Web Development (281)
Areas Of Interest
Authors Area
Are you a software author? Take a look at our Author Resource Center where you will find marketing tools, software specifically created for promoting your software and a ton of other helpful resources.
Dark Files 6.2.1.1
Security & Privacy :: Access Control
Dark Files can help you keep your files protected. You can choose who gets access to what files on your computer. This program provides three levels of protection to suit any user : "Hidden", "Read Only", "Full Control". It works with any Windows platforms : 2000/XP/Seven . Dark Files can work with Network folders and fully supports protection of removable media (such as floppies, CD Roms, DVD, ZIP and some SCSI and RAID drives) on all platforms. This easy-to-use program allows you to protect your files and folders (including subdirectories) in various ways. You can hide them or prevent others from deleting, renaming, executing, or modifying your files in any way. The Wildcard feature allows you to specify which files you want to protect (for example, all EXE or DLL files). The file system protection works independently of the program , so if you even close the program the file protection will still work. Built-in support for multiple user interface allows you to use Dark Files without any change on multi user systems. You can define own settings for each user separately or just define settings for the "Guests group" . If your computer is configured for using by multiple users you can define the list of protected folders separately for each user. If some user has not got own settings the program will apply settings of the "Guests group" to that user. If you are looking for a solid file protection program, look no further.
Specifications:
Version: 6.2.1.1 |
Download
|
Similar Products:
ARMORTOOLS PROFESSIONAL 26.2.1
Security & Privacy :: Encryption Tools
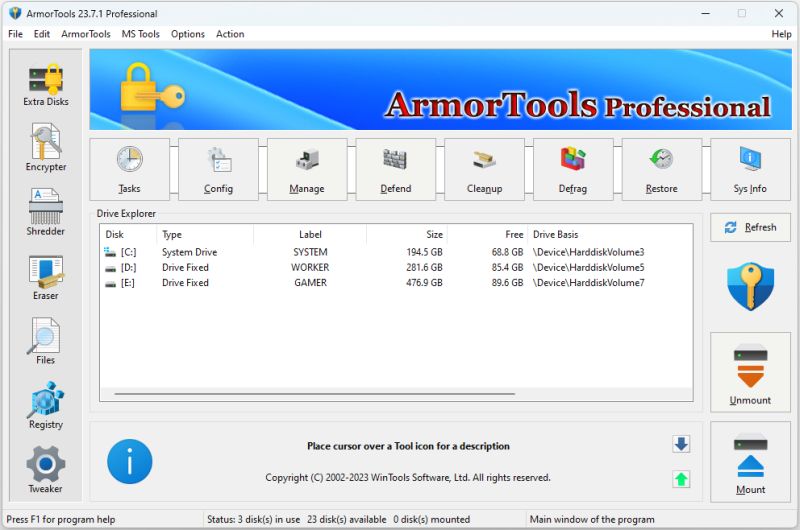 ArmorTools Professional is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
ArmorTools Professional is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
Windows | Shareware
Read More
Security & Privacy :: Encryption Tools
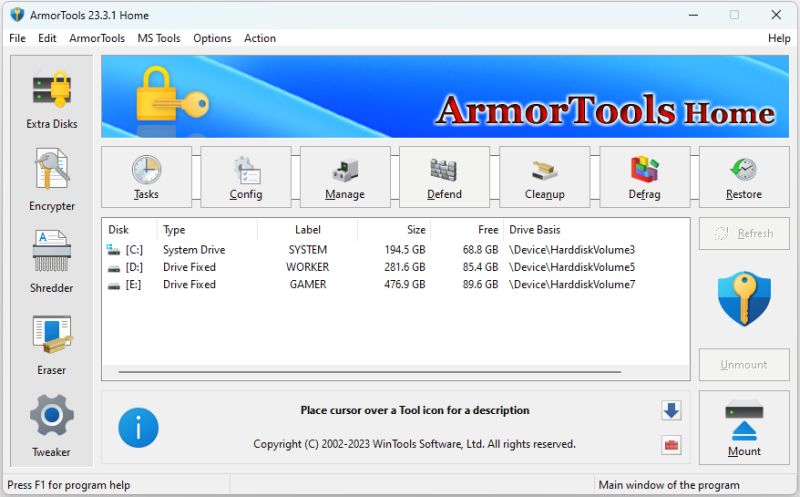 ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
Windows | Shareware
Read More
Security & Privacy :: Encryption Tools
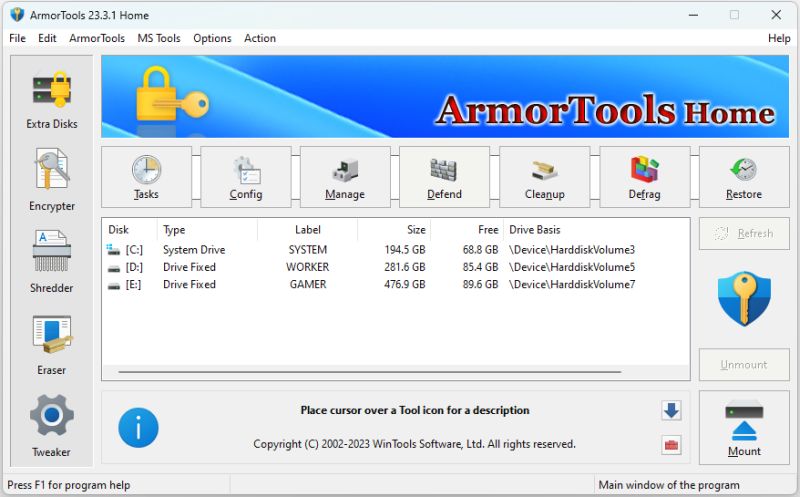 ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
Windows | Shareware
Read More
Security & Privacy :: Encryption Tools
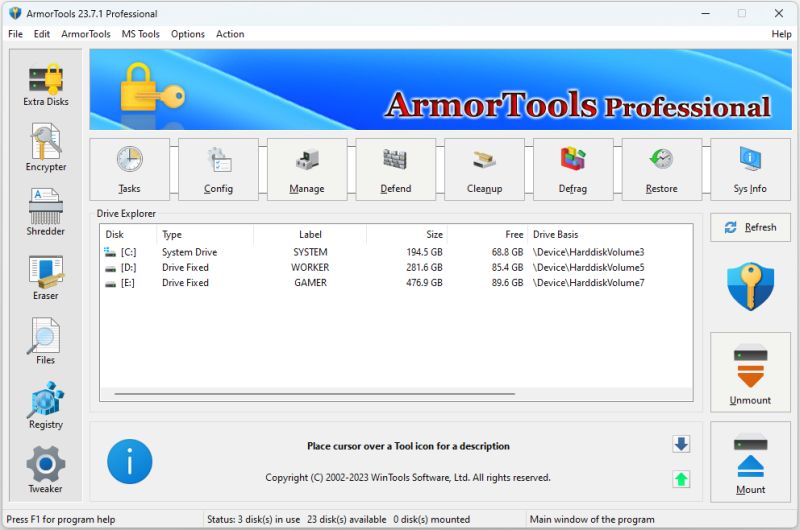 ArmorTools Pro is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools Pro allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools Pro removes traces of the user's work on the computer, clears the history of visiting sites...
ArmorTools Pro is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools Pro allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools Pro removes traces of the user's work on the computer, clears the history of visiting sites...
Windows | Shareware
Read More




