Search N5 Net Software Repository:
Search Files
Sponsor:
Browse:
- Audio & Multimedia (1565)
- Business (1732)
- Communications (466)
- Desktop (182)
- Development (569)
- Education (166)
- Games & Entertainment (707)
- Graphic Apps (683)
- Home & Hobby (105)
- Network & Internet (543)
- Security & Privacy (500)
- Servers (65)
- System Utilities (9315)
- Web Development (281)
Areas Of Interest
Authors Area
Are you a software author? Take a look at our Author Resource Center where you will find marketing tools, software specifically created for promoting your software and a ton of other helpful resources.
Downloading JOC History Eraser 1.0.1.9
Your download will begin in a few seconds. If it does not start you can download directly through one of the mirror sites below.
- Mirror Site 1: http://www.jocsoft.com/files/joche.exe
- Mirror Site 2: http://www.bot21.com/files/joche.exe
Get Details for JOC History Eraser 1.0.1.9
Similar Products:
ARMORTOOLS PROFESSIONAL 26.2.1
Security & Privacy :: Encryption Tools
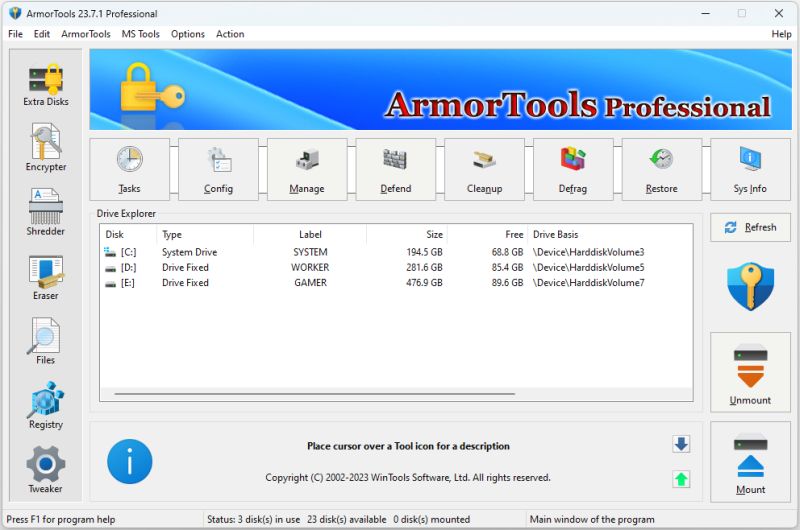 ArmorTools Professional is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
ArmorTools Professional is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
Windows | Shareware
Read More
Security & Privacy :: Encryption Tools
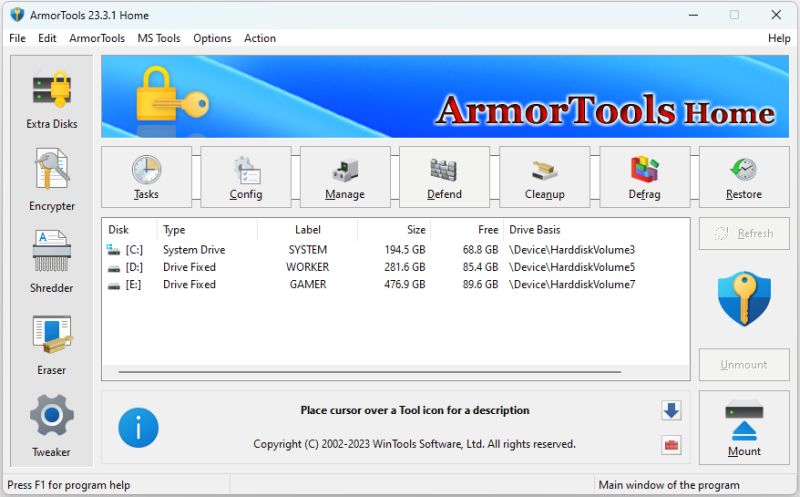 ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
Windows | Shareware
Read More
Security & Privacy :: Encryption Tools
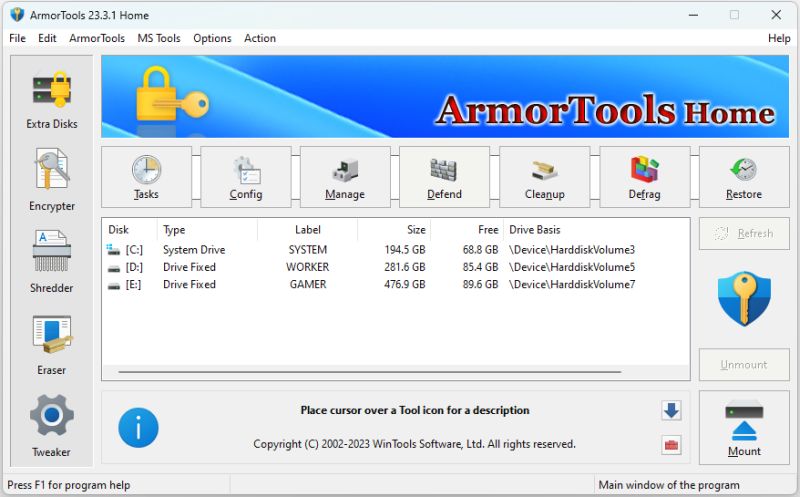 ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
Windows | Shareware
Read More
Security & Privacy :: Encryption Tools
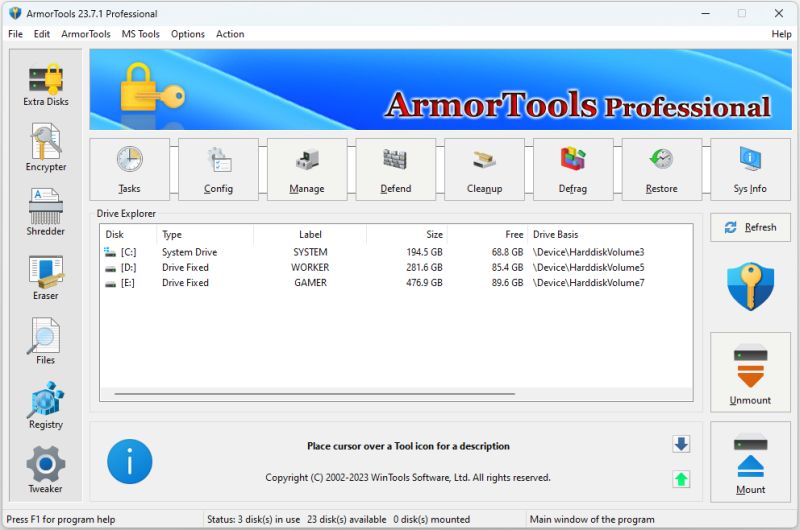 ArmorTools Pro is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools Pro allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools Pro removes traces of the user's work on the computer, clears the history of visiting sites...
ArmorTools Pro is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools Pro allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools Pro removes traces of the user's work on the computer, clears the history of visiting sites...
Windows | Shareware
Read More
Security & Privacy :: Encryption Tools
 ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
ArmorTools is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools removes traces of the user's work on the computer, clears the history of visiting sites...
Windows | Shareware
Read More
ARMORTOOLS PROFESSIONAL X64 26.2.1
Security & Privacy :: Encryption Tools
 ArmorTools Pro x64 is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools Pro x64 allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools Pro removes traces of the user's work on the computer, clears the history of visiting sites...
ArmorTools Pro x64 is a set of tools that expands the capabilities of the MS Windows operating system in the field of security and protection of user confidential information. ArmorTools Pro x64 allows you to create secure virtual disks encrypted using AES128/AES256 algorithms, encrypt files and folder contents using any file as a password. ArmorTools Pro removes traces of the user's work on the computer, clears the history of visiting sites...
Windows | Shareware
Read More
ALLMYNOTES ORGANIZER DELUXE EDITION 4.16
Business :: PIMS & Calendars
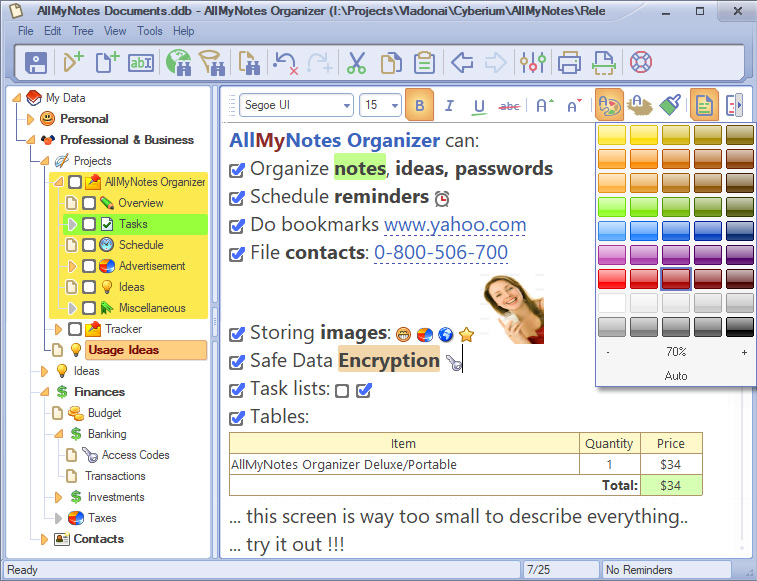 AllMyNotes Organizer Deluxe - your ultimate software for safeguarding your entire information library. Your digital life deserves protection - manage it like your legacy! With AllMyNotes Organizer Deluxe, each piece of your private knowledge is securely saved in a encrypted vault offline Unlike online services that charge recurring charges, AllMyNotes Organizer Deluxe is yours to keep - no monthly charges at all! Purchase once own forever!
AllMyNotes Organizer Deluxe - your ultimate software for safeguarding your entire information library. Your digital life deserves protection - manage it like your legacy! With AllMyNotes Organizer Deluxe, each piece of your private knowledge is securely saved in a encrypted vault offline Unlike online services that charge recurring charges, AllMyNotes Organizer Deluxe is yours to keep - no monthly charges at all! Purchase once own forever!
Windows | Shareware
Read More
RECOVER EXCEL WORKSHEET PASSWORD 5.5
System Utilities :: File & Disk Management
 Need to Recover forgotten Excel Password? You are at right place! Perfect Data Solutions Excel password recovery will easily break excel password or unprotect excel sheet. Recover Excel Worksheet Password instantly with PDS Excel Password Recovery tool using Brute force & Dictionary attack method. Excel Password Recovery Demo version show you first 3 character password. Recover Excel file password from MS Excel 97 to 2016.
Need to Recover forgotten Excel Password? You are at right place! Perfect Data Solutions Excel password recovery will easily break excel password or unprotect excel sheet. Recover Excel Worksheet Password instantly with PDS Excel Password Recovery tool using Brute force & Dictionary attack method. Excel Password Recovery Demo version show you first 3 character password. Recover Excel file password from MS Excel 97 to 2016.
Windows | Shareware
Read More
Security & Privacy :: Password Managers
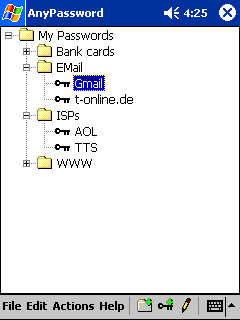 Entrust your passwords to Pocket AnyPassword. Now your passwords can be kept secure in your pocket PC. The utility organizes all data as a system of folders and subfolders, where you can get what you need within seconds - an advanced search option is at your service. All passwords are protected by the RC2/MD5 encryption algorithms. Added to this is a multi-user support, a password generator and synchronization with a desktop PC.
Entrust your passwords to Pocket AnyPassword. Now your passwords can be kept secure in your pocket PC. The utility organizes all data as a system of folders and subfolders, where you can get what you need within seconds - an advanced search option is at your service. All passwords are protected by the RC2/MD5 encryption algorithms. Added to this is a multi-user support, a password generator and synchronization with a desktop PC.
Windows | Freeware
Read More


