Search N5 Net Software Repository:
Search Files
Sponsor:
Browse:
- Audio & Multimedia (1565)
- Business (1732)
- Communications (466)
- Desktop (182)
- Development (569)
- Education (166)
- Games & Entertainment (707)
- Graphic Apps (683)
- Home & Hobby (105)
- Network & Internet (543)
- Security & Privacy (500)
- Servers (65)
- System Utilities (9315)
- Web Development (281)
Areas Of Interest
Authors Area
Are you a software author? Take a look at our Author Resource Center where you will find marketing tools, software specifically created for promoting your software and a ton of other helpful resources.
Downloading Crypto 4.4a
Your download will begin in a few seconds. If it does not start you can download directly through one of the mirror sites below.
- Mirror Site 1: http://www.kmrconsulting.com/download/crypto/crypto.exe
- Mirror Site 2: http://www.cs.rit.edu/~kar/download/crypto.exe
Get Details for Crypto 4.4a
Similar Products:
BATCH FILE ENCRYPT FREE 5.0.135
Security & Privacy :: Encryption Tools
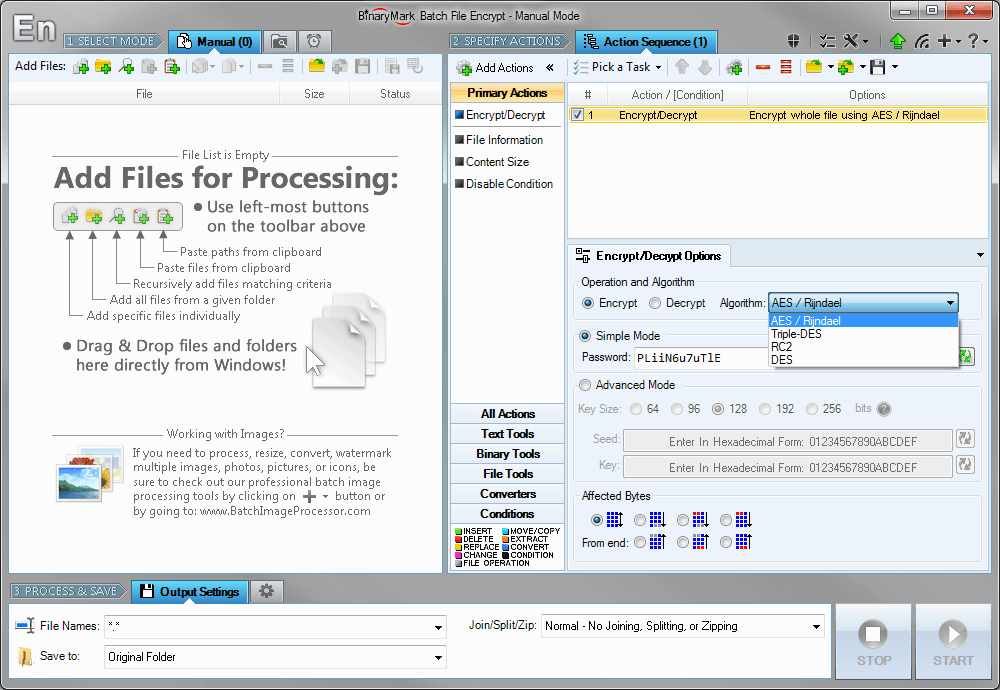 Encrypt and decrypt whole files or their parts using AES, Triple-DES (3DES), RC2, and DES symmetric algorithms. You can encrypt files with a single password or specify cryptographic keys (vectors) instead. You can change key bit length for better protection. You can select specifically which bytes in a file should be encrypted/decrypted, though by default the whole file is processed.
Encrypt and decrypt whole files or their parts using AES, Triple-DES (3DES), RC2, and DES symmetric algorithms. You can encrypt files with a single password or specify cryptographic keys (vectors) instead. You can change key bit length for better protection. You can select specifically which bytes in a file should be encrypted/decrypted, though by default the whole file is processed.
Windows | Shareware
Read More
Security & Privacy :: Encryption Tools
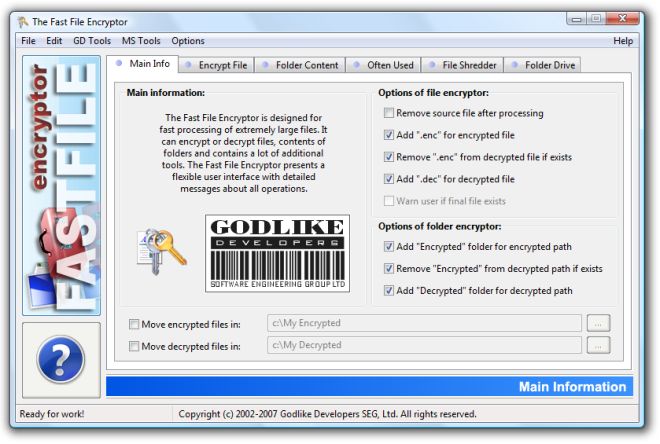 Fast File Encryptor is MS Windows compatible software designed for fast processing of extremely large files. It can encrypt and decrypt files, contents of folders using any file as a password. Fast File Encryptor contains a lot of additional tools and presents a flexible user interface with detailed messages about all operations. Fast File Encryptor compatible with ArmorTools software.
Fast File Encryptor is MS Windows compatible software designed for fast processing of extremely large files. It can encrypt and decrypt files, contents of folders using any file as a password. Fast File Encryptor contains a lot of additional tools and presents a flexible user interface with detailed messages about all operations. Fast File Encryptor compatible with ArmorTools software.
Windows | Shareware
Read More
System Utilities :: File & Disk Management
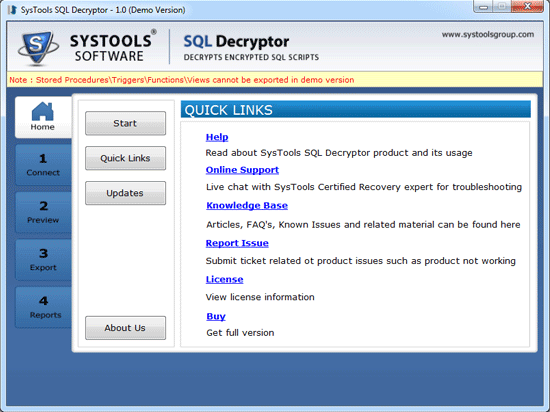 If you need perfect and reliable solution for decrypt encrypted SQL script file, then you can choose this SQL decryptor tool which is result-oriented and safe tool that decrypt SQL script file and gives the preview of views, triggers, functions and store procedures without any error. Know how to decrypt encrypted SQL Script files with SQL Server database decryption tool.
If you need perfect and reliable solution for decrypt encrypted SQL script file, then you can choose this SQL decryptor tool which is result-oriented and safe tool that decrypt SQL script file and gives the preview of views, triggers, functions and store procedures without any error. Know how to decrypt encrypted SQL Script files with SQL Server database decryption tool.
Windows | Shareware
Read More
Security & Privacy :: Encryption Tools
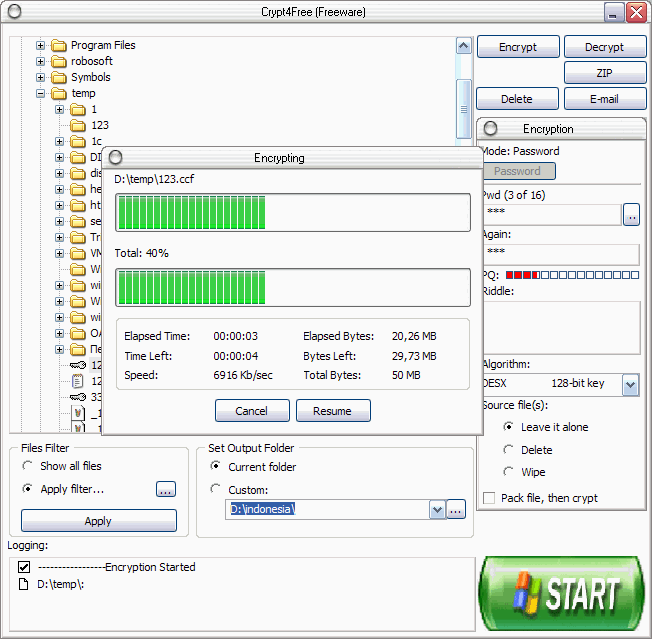 Crypt4Free (freeware) is files encryption software with ability to encrypt files and text messages. Support for ZIP files and ability to secure delete sensitive files. Skinnable user friendly interface.The latest version includes "Privacy Master" tool to erase all personal traces on computer.
Crypt4Free (freeware) is files encryption software with ability to encrypt files and text messages. Support for ZIP files and ability to secure delete sensitive files. Skinnable user friendly interface.The latest version includes "Privacy Master" tool to erase all personal traces on computer.
Windows | Freeware
Read More
ADVANCED ENCRYPTION PACKAGE 2008 PROFESSIONAL 4.8.7
Security & Privacy :: Encryption Tools
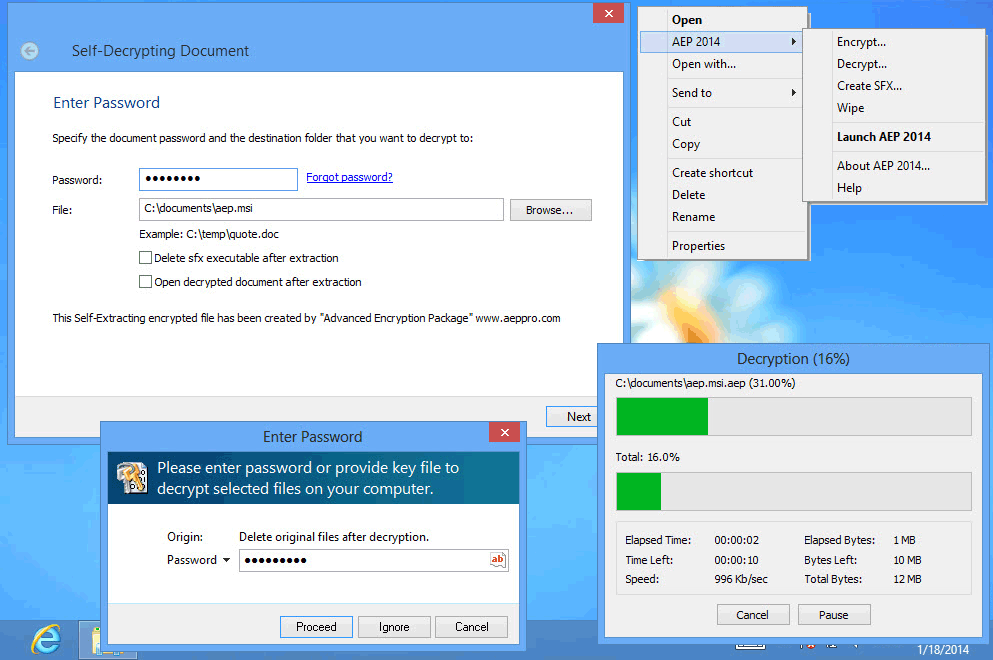 AEP2008 PRO most noteworthy feature may be its flexibility and military grade encryption: program includes 17 encryption algorithms (AES, TWOFISH, MARS, etc). 18 secure files erasure algorithms including: U.S. DoD 5200.28, GOST P50739-95 and others. Symmetric and RSA encryption using PKI infrastructure. USB Flash Drives as protected Passwords Storage support. Command Line Support. No special encryption knowledge is required to use this software!
AEP2008 PRO most noteworthy feature may be its flexibility and military grade encryption: program includes 17 encryption algorithms (AES, TWOFISH, MARS, etc). 18 secure files erasure algorithms including: U.S. DoD 5200.28, GOST P50739-95 and others. Symmetric and RSA encryption using PKI infrastructure. USB Flash Drives as protected Passwords Storage support. Command Line Support. No special encryption knowledge is required to use this software!
Windows | Shareware
Read More
System Utilities :: File & Disk Management
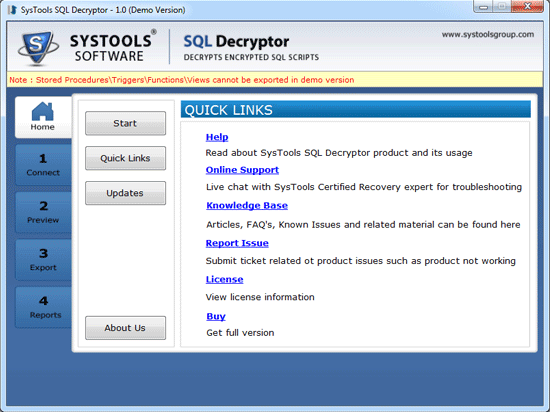 SQL Decryptor as name specify decryptor whose task to change the database into readable form by performing decryption process on the SQL scripts of SQL Server 2008 or SQL Server 2005. SQL Decryptor software is mainly used for security purpose which removes encryption from SQL Scripts present in the SQL elements. SQL user?s data is in encrypted form to protect it from the hacking.
SQL Decryptor as name specify decryptor whose task to change the database into readable form by performing decryption process on the SQL scripts of SQL Server 2008 or SQL Server 2005. SQL Decryptor software is mainly used for security purpose which removes encryption from SQL Scripts present in the SQL elements. SQL user?s data is in encrypted form to protect it from the hacking.
Windows | Shareware
Read More
Security & Privacy :: Encryption Tools
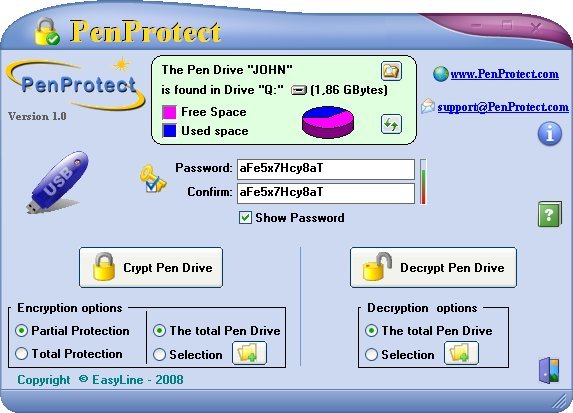 PenProtect is the most comprehensive and secure solution to protect the files within your USB Flash Drive, Flash Memory or Pen Drive. Files are encrypted and protected using your Password and a special technique (AES algorithm 256 bit key). PenProtect requires no installation. It is a single file located in the home folder of your Flash Drive. Ability to encrypt or decrypt only required files. No size limit of encrypted files.
PenProtect is the most comprehensive and secure solution to protect the files within your USB Flash Drive, Flash Memory or Pen Drive. Files are encrypted and protected using your Password and a special technique (AES algorithm 256 bit key). PenProtect requires no installation. It is a single file located in the home folder of your Flash Drive. Ability to encrypt or decrypt only required files. No size limit of encrypted files.
Windows | Demo
Read More
Security & Privacy :: Encryption Tools
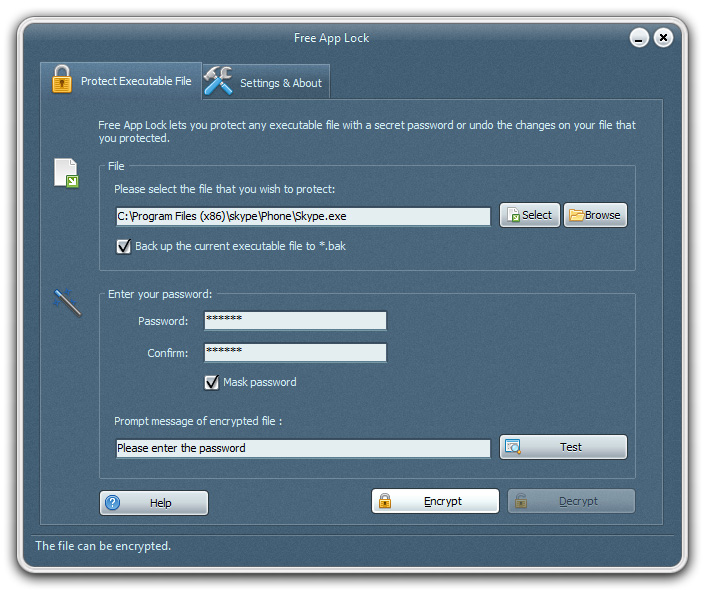 Free App Lock is an innovative application encryptor, which allows you to lock any executable programs with password from non-authorized execution to block other clients from modifying the variables stored in the Application object to protect your privacy. Now, there is no need to worry about others will use your tax preparation software, personal finance or other programs and so on.
Free App Lock is an innovative application encryptor, which allows you to lock any executable programs with password from non-authorized execution to block other clients from modifying the variables stored in the Application object to protect your privacy. Now, there is no need to worry about others will use your tax preparation software, personal finance or other programs and so on.
Windows | Freeware
Read More
::
 PDF Password Finder can be used to decrypt protected Adobe Acrobat PDF files, which have "owner" password set, preventing the file from editing (changing), printing, selecting text and graphics (and copying them into the Clipboard), or adding/changing annotations and form fields. Decryption is being done instantly. Decrypted file can be opened in any PDF viewer (e.g. Adobe Acrobat Reader) without any restrictions.
PDF Password Finder can be used to decrypt protected Adobe Acrobat PDF files, which have "owner" password set, preventing the file from editing (changing), printing, selecting text and graphics (and copying them into the Clipboard), or adding/changing annotations and form fields. Decryption is being done instantly. Decrypted file can be opened in any PDF viewer (e.g. Adobe Acrobat Reader) without any restrictions.
Windows | Shareware
Read More


